By 2025, cybersecurity threats originating from the dark web are projected to rise sharply, with small and medium-sized businesses (SMBs) among the most vulnerable. Reports indicate that more than 60% of SMBs targeted by cyberattacks shut down within six months, often due to exposed credentials or financial fraud linked to dark web activity. Cybercriminals are leveraging artificial intelligence to automate attacks, refine phishing strategies, and exploit security vulnerabilities faster than businesses can respond.

How To Stay Safe On The Dark Web?
Easily initiate data encryption on your external drives and disks, ensuring compliance with your specific company policies. Encryption-2-Go offers controlled encryption, container-based or directory encryption, and even detects existing BitLocker To Go encrypted drives. With configurable user selection dialogs, it provides a user-friendly experience while maintaining strict security.

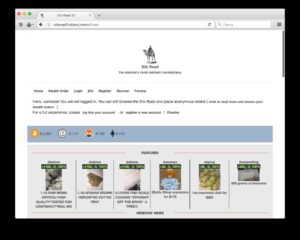
Top Dark Web Marketplaces Of 2025: A Deeper Dive Into Illicit Trade Markets
Remember that illegal activities can still incriminate you, whether you are using a Tor browser. For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography. Nowadays, many people use the Tor browser to surf the public internet and navigate the deeper parts anonymously. Some markets even sell privacy tools, but you are more likely to run across counterfeit prescription pills and stolen identities.
What’s The Difference Between The Deep Web, Dark Web, And Tor?
- In some authoritarian states, accessing Tor nodes can flag you for surveillance.
- Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble.
- It can be very beneficial for users but there is also a very big downside.
- Using a virtual private network (VPN) masks your real IP by routing your internet traffic through a secure server, making it appear as though you’re browsing from a different location.
- It supports operations in multiple languages and operates on both clearnet and Tor.
It’s still illegal to commit crimes while connected to Tor, regardless of whether or not you think you’ll be caught. Without further ado, let’s take a look at some of the best tor and onion links for you to check out, in no particular order. That’s why it’s important to verify links through trusted directories and proceed with caution. While the best dark web sites listed above are a good starting point for a safe, legal surfing experience on Tor, there really is no substitute for a VPN. Many dark web links could get you mixed up in some kind of criminal activity of another, whether you’re looking for it or not. The deep web is rife with sales of illicit drugs, weapons, and goodness knows what else, and steering clear of these nefarious web pages is easier said than done.
Ransomware Threat Actors
Let’s break down how to find dark web sites (also known as .onion sites) safely and easily in 2025. With the wealth of stolen data circulating in hidden forums and marketplaces, there’s a heightened risk of data breaches and operational disruptions. Even casual mentions of a company in dark web circles can serve as a prelude to an attack. Onion sites have multiple malware-loaded mirror sites and show dangerous ads or external links that can redirect you to phishing scam sites.
Best Practices For Staying Safe
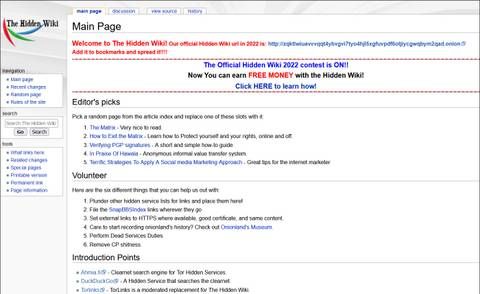
This hidden realm, often referred to as the Dark Web, is accessed through specialized browsers like Tor. Now that there are organizations that employ trained and certified cybersecurity experts to detect vulnerabilities and gaps, hackers have other motivations. The evolution of these motivations really goes hand-in-hand with the evolution of hacking, in general. Schools and other educational institutions were the number-one most attacked market in 2022 according to Check Point Research, seeing a 43% increase compared to 2021.
Dark Web Links For Email Services

Dark web marketplaces are hubs where vendors sell everything from digital tools to physical goods. While some of these markets operate legally within certain jurisdictions, many are known for illegal activity. For this reason, they are often short-lived and heavily targeted by law enforcement. Users should be extremely cautious when exploring this category, as fake markets and scams are widespread. No marketplace should ever be trusted blindly, even if it looks professional.
Artificial intelligence is now being weaponized to conduct more effective attacks. Threat actors can execute highly targeted and scalable attacks with minimal effort as more tools become accessible and easier to use. As a result of more threat actors using malicious AI in their cyberattacks, 75% of cybersecurity professionals had to modify their strategies last year to address AI-generated incidents. First and foremost, it is important to use a reliable virtual private network (VPN) while accessing the dark web. A VPN will help protect your identity and data by encrypting your internet connection and hiding your IP address.
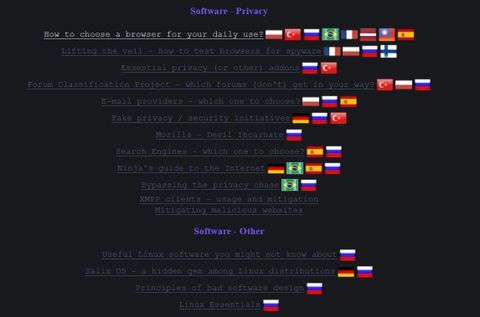
SecureDrop is an open-source submission system that nonprofit organizations (NGOs), journalists, and news organizations can use to share and receive sensitive files securely. It’s used by 50+ news organizations, including ABC, Bloomberg News, CBC, and The New York Times. A robust antivirus can help block malware and other online threats, even on the dark web. Additionally, the advent of quantum computing poses potential threats to current encryption standards, necessitating a reevaluation of security protocols. Concurrently, cybercriminals have increasingly exploited valid credentials to infiltrate networks.
Hacking tools, phishing kits, ransomware, and other forms of malicious software are readily available on the dark web. These tools can be used by attackers with little technical knowledge to carry out damaging cyberattacks. The dark web, on the other hand, is defined as the subdivision of the deep web.
Popular Dark Web Links & Websites
The basic architecture of a standard web crawler, such as those used by Google, relies on indexing from seed URLs, analyzing metadata, and following link structures. This process doesn’t work on the dark and deep web, where most sites are not interlinked. Plus, many .onion websites are created to be temporary or invite-only, so they may not even be active long enough to be indexed. FreeHacks, a Russian-based forum, is one of the largest hacking communities in the world. Since its creation in 2014, it has become known for providing an extensive database of hacking tools and resources. The forum primarily focuses on carding, DDoS attacks, and other forms of cybercrime.
Whistleblower platforms enable confidential document submission without compromising the identity of sources. GlobaLeaks is an open-source platform designed for NGOs and media to create customizable submission portals, emphasizing decentralization and anonymity. StrongBox adds advanced metadata stripping and encrypted messaging features, increasing whistleblower protection.
While dark web search engines are essential for accessing the dark web and monitoring potential threats to your business, they are not without their own risks. Each search engine opens the door to potentially harmful content, making caution a necessity. Though not a search engine in the traditional sense, OnionLinks is a categorized directory of verified .onion websites. It organizes links into sections like forums, blogs, marketplaces, and privacy tools. Because of its structured directory format, OnionLinks is often included in lists of dark web search tools.
However, many are used for illegal activity and onion websites are often popular hangouts for cybercriminals and scammers. Using common sense like avoiding clicking on shady links or download buttons, sticking to known sites and adding a VPN for an extra layer of protection, you should be fine. You can tell you’re on the dark web if you’re accessing websites with .onion addresses on the Tor Browser or a similar anonymity network. These sites aren’t accessible via standard web browsers or search engines. Users can explore onion sites easily and search for content without having to know any specific onion links in advance. You’ll keep your identity private while getting results for various Tor websites, forums, and marketplaces.
Download And Install The Tor Browser
The website’s articles focus on digital rights, surveillance, and security research. I found their technical explanations clear and well-researched, though the site updates less frequently than other news platforms. Although some of these markets prohibit certain extreme content such as violence or exploitation, most operate with very few rules beyond ensuring the security and anonymity of their users.