That said, cybercriminals increasingly target this part of the internet because of the lucrative personal data lying within. That’s why basic online hygiene has become critical to protecting yourself online. Unlike the Dark Web, sites on the Deep Web can be accessed using normal web browsers like Firefox, Google Chrome, and Safari. Also, these sites are often linked to publicly accessible pages, making them findable and accessible by users with the right login credentials and willingness to pay.
- Diving into the depths of the Internet isn’t for the faint of heart, especially regarding the Dark Web and Deep Web.
- Log360 integrates with Constella Intelligence, the AI-driven identity intelligence provider, to continuously monitor dark web for security threats.
- The deep web doesn’t use unique methods to hide or serve content — it uses the same technologies the surface web relies on.
- Moreover, the anonymity that protects users can also be a double-edged sword.
- This exposure can lead to legal repercussions if law enforcement tracks illegal activities back to you, despite the anonymity.
- The Dark Web is a segment of the Deep Web, which typically hosts illegal affairs, but not everything on it is illegal.
Get The Latest Cybersecurity News And Updates Sent Straight To Your Inbox
Unlike the deep web vs dark web that encompass such secrecy or illegality, this surface web is totally safe to be used daily as well as it falls under more familiar laws and regulations. Hence, while the face of the internet remains the surface web, the deep and dark web are the hidden layers of the internet that require caution and understanding to traverse. Perhaps the most notorious of the dark web sectors, it is indeed infamous for hosting illicit content, which contains marketplaces trading everything from drugs and weapons to stolen data. Also contained within it are forums for discussion that include everything from hacking services to human trafficking. The deep web and dark web have many uses, but they also come with risks.
How To Keep Your Information Safe On The Deep Web And Dark Web
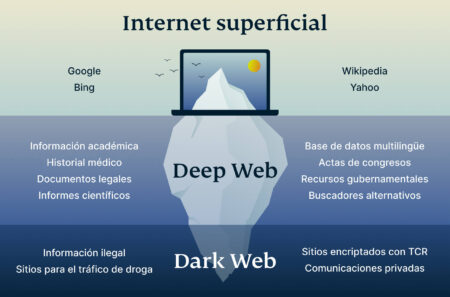
The dark and deep web layers are also not as easily monitored by regulatory bodies. The top layer is the web which is accessible by default when you purchase the services of an ISP (Internet Service Provider). It can be accessed by using major search engines such as Yahoo, Google and Bing. This version of the web is used by most of the world’s population for shopping, banking, entertainment and receiving the latest news. It is also heavily monitored by the world’s intelligence agencies and law enforcement on behalf of their governments. In today’s digitally interconnected world, confusion frequently arises around the terms dark web vs deep web.
Risks Of Accessing The Deep Web Vs The Dark Web
Another category of dark web users includes journalists and whistleblowers who want to share confidential or sensitive information without fear of censorship or legal action. The Deep Web encompasses all online content that standard search engines like Google, Bing, or Yahoo cannot index. These hidden areas of the internet typically require some form of authentication or specialized access to view, making them invisible to general web crawlers. Contrary to popular belief, the Deep Web doesn’t solely exist for illicit purposes—in fact, a large portion of it is entirely legal and critical for day-to-day operations in the digital world.
Understanding The Layers Of The Web
The web pages on the deep web are protected by credentials, paywalls, and are intentionally made private. However, these websites can still be accessed using common web browsers like Chrome or Firefox by knowing the URL of the page and the necessary credentials. Content that resides on the surface web is accessible because software robots called “spiders” or “crawlers” capture and index it, and search engines assign it rankings. These systems typically scan websites that contain .com, .org., .net, or a similar domain as well as some data and posts at social media sites.
Darknet Communications In 2025 – From IRC Forums To Telegram Crime Networks
These two terms often get tossed around interchangeably, but they represent very distinct layers of the internet. Safe and reliable Internet access protected against malicious activity. Our local team of cybersecurity experts are ready to help you immediately. In short, the Deep Web is simply the private part of the internet, where you need to log in to access information. The Deep Web and the Dark Web are often lumped together, but in reality, they’re quite different worlds.
The Key Differences Between The Deep Web And Dark Web
The dark web refers to encrypted online content that is not indexed by conventional search engines. Darknet provides a user with anonymity but service was introduced that allowed someone to host a website on the darknet and remain anonymous. This attracted people who do illegal stuff to sell things without getting caught. One example is a website called the silk road which was on a darknet called TOR, used to sell drugs, and was taken down by the FBI.

What Precautions Should Be Taken When Accessing The Dark Web?
While the idea certainly sounds noble, criminals worldwide were quick to recognize and take advantage of the anonymity it offers. Unlike the publicly accessible surface web, the deep web includes sites requiring login credentials but is still accessible via traditional browsers. The dark web is a small, hidden subset of the deep web that requires special tools to access. The dark web is home to all sorts of illicit activities and is considered unsafe. As mentioned earlier, regular browsers cannot access dark web websites.
Examples Of Deep Web Content:
This part of the web is infamous for its Dark Web criminal activities, from drug trafficking to espionage. In fact, it is likely some 500 times larger than the surface web and may contain as much as 96 percent of online content. Much of this content is in the form of databases that are accessible only by password or subscription or for a fee. The internet is vast, but much of it lies hidden beneath the surface. Dive into the intriguing world of the Deep Web and Dark Web to understand their differences, purposes, and potential risks. Whether you’re curious about the hidden layers of the web or seeking clarity on popular myths, this guide will demystify the unseen side of the internet.
However, all those endorsements still don’t seem to have convinced some world leaders about the importance of online anonymity. Former British Prime Minister, David Cameron, was a vocal critic of end-to-end encryption employed by apps like WhatsApp and Snapchat, and actually even tried to rope in the then-U.S. U.S. law enforcement agencies have also expressed deep reservations about encryption software, most notably after the San Bernardino attack a couple of years ago. Unfortunately, some sections of the media have often seemed confused about the Deep Web, and what the term actually means. So you’ve heard the terms ‘Deep Web’ and ‘Dark Web’ thrown around in the media of late, and the latest bust of the the notorious ‘AlphaBay Market’ probably piqued your interest in the topic as well.
Use Tor browser on a separate device, enable VPN for added anonymity, disable scripts, avoid downloading files, never reveal personal information, and follow organizational security policies. This solution enables security teams to identify and remediate potential threats at the reconnaissance phase, significantly reducing breach risk. Technical considerations here involve encryption strength; weak implementations undermine the very privacy this layer seeks to protect. The Deep Web thus balances safeguarding data with the practicalities of access, a dynamic critical to modern digital operations. However, it poses challenges for collaboration; sharing Deep Web resources across organizations requires secure, standardized protocols. In general, the rules for accessing the deep web and the dark web safely are similar to the best practices for accessing the surface web.
Additionally, the dark web can pose a threat even to those who don’t mess with it. The reason for this is because the primary transacted good is the data of users. There are gigabytes worth of information in the form of leaked data that is for sale. This leaked data helps hackers and other cybercriminals get the info needed for identity theft, stuffing attacks and nefarious activities of all kinds.