Our research details a thriving underground economy and illicit supply chain enabled by darknet markets. As long as data is routinely stolen, there are likely to be marketplaces for the stolen information. Launched in 2020, Cypher Marketplace sells fraudulent documents, stolen credit cards, fake IDs, and malware. Its emphasis on user anonymity and document forgery makes it a core tool for identity fraud. Launched after the takedown of AlphaBay in 2021, Abacus Market has rapidly risen to prominence. It features over 40,000 listings including narcotics, counterfeit items, hacking tools, and stolen data.
Hidden Data Trade
These archives are xz-compressed tarballs (optimized with the sort-key trick); typically each subfolder is a single date-stamped (YYYY-MM-DD) crawl using wget, with the default directory/file layout. (Child porn is not a concern as all DNMs & DNM forums ban that content.) Archives sourced from other people follow their own particular conventions. Mac & Windows users may be able to uncompress using their built-in OS archiver, 7zip, Stuffit, or WinRAR; the PAR2 error-checking can be done using par2, QuickPar, Par Buddy, MultiPar or others depending on one’s OS. A repository preserving darknet market data, including vendor lists, PGP keys, listings, and more for research & intelligence purposes. One of the most notorious Dark Web incidents occurred in October 2013, when the FBI shut down Silk Road, the then-largest Dark Web marketplace. Founded by Ross William Ulbricht in 2011, Silk Road quickly established itself as the go-to destination for illegal items, particularly illegal drugs.
However, anonymous browsers are banned in China, while Russia and some other countries actively block their citizens from using them. Yes, the Dark Web exists as a small subset of the Deep Web — part of the internet that isn’t indexed by search engines and thus isn’t publicly available. Experts estimate that the Dark Web accounts for no more than 5% of the entire internet. While it’s impossible to say precisely how many people regularly access the Deep Web and the Dark Web, looking at the number of Tor users could help paint a clearer picture. Between July 1 and September 30, 2023, this anonymous browser averaged over 4.61 million daily users, with more than 4.45 million connecting to it directly. During the same period, another 158,530 people connected to the browser via undisclosed servers.
Most Internet Users Rely On The Tor Browser To Access The Dark Web
These often contain login credentials that have been stolen by malware on infected systems. Another relevant section is Cracked Accounts, where compromised user accounts for various online services are published. There is also a section called Combolists, where lists of username/password combinations are shared that can be used for credential stuffing attacks.
Scams And Fraudulent Activities On The Darknet Markets
This service is a good source of statistics if you have a school project requiring research on Tor and the dark web. However, note that the site only uses non-sensitive and public data for the metrics. Even without monitoring your browsing activities, DuckDuckGo will offer decent answers to your questions. DeSnake joined the conversation, creating an account with his moniker on September 12, 2021 in attempts to mitigate the marketplace’s potential reputation damage. DeSnake repeatedly pointed to their vouches from Dread and old PGP key pasted to Ghostbin, paste site. DarkOwl has been unable to assess how the larger darknet community (outside of Dread) feels about the new Alphabay Market.
In the summer of 2017, a team of cyber cops from three countries successfully shut down AlphaBay, the dark web’s largest source of contraband, sending shudders throughout the network. Medical records, fee-based content, membership websites, and confidential corporate web pages are just a few examples of what makes up the deep web. Estimates place the size of the deep web at between 96% and 99% of the internet. Only a tiny portion of the internet is accessible through a standard web browser—generally known as the “clear web”. In 2019, the FBI started its investigation into Genesis Market and enlisted other government agencies and law enforcement organizations across the world, working towards the market’s closure on April 4, 2023.
The darknet is used for anonymous communication, accessing censored information, and protecting privacy. Journalists and activists use it to communicate securely in oppressive regimes. You can access it for legitimate purposes like whistleblowing and freedom of expression. However, it’s also used for illegal activities like drug trafficking, weapon sales, and stolen data trading. Law enforcement agencies monitor it for criminal activities, but legitimate users rely on it for privacy protection.
- Disappeared with funds; based on a screenshot of categories, seems to have been almost exclusively drugs.
- There are often copious amounts of how-to articles, software exploits, and hacked credentials for sale.
- This network of over 6,000 relays hides your location, thus protecting you from online surveillance and third-party tracking by your websites.
- The biggest and most frustrating part about dark websites is that they live for a short span of time.
- This ongoing cat-and-mouse game poses a significant technical challenge in combating the activities within darknets.
Federal Financial Data
Unlike the Deep Web, Darknets are intentionally hidden and designed to preserve privacy and anonymity. There are estimated to be 1.1 billion websites on the Surface Web as of 2025 (Internet Live Stats). You’re only scratching the surface when you use the Internet for daily activities—reading news, managing finances, running businesses. Search engines like Google, Bing, and Yahoo can access just about 4% of the web.
Legitimate Use Cases For The Average User
Researchers Daniel Moore and Thomas Rid of King’s College in London classified the contents of 2,723 live dark web sites over a five-week period in 2015 and found that 57% host illicit material. Darknet markets were one of two categories of crypto crime that saw revenues rise in 2023. In total, darknet markets and fraud shops received $1.7 billion last year, a rebound from 2022 — the year that saw the sizable Hydra Marketplace close. The ensuing war for darknet market dominance that began in 2022 continued into 2023, but no other market has since matched Hydra’s financial success.
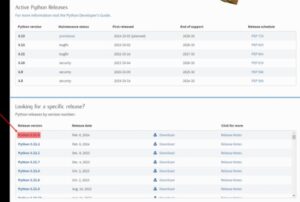
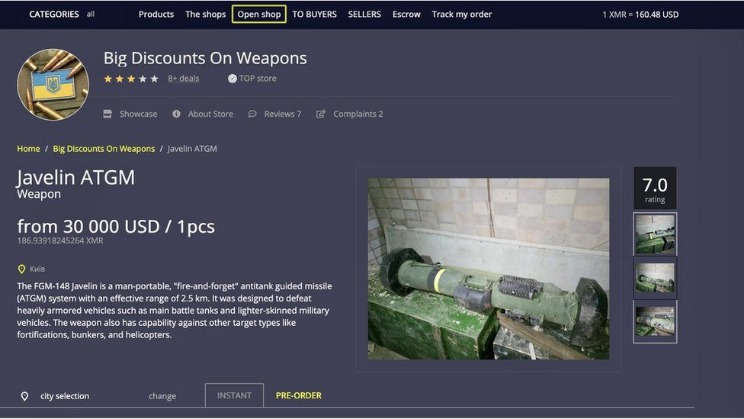
Best Dark Web Marketplaces – Detailed List
Furthermore, darknet users rarely draw so much attention to themselves. DeSnake has broken this mold with their dramatic return to the public eye that included interviews with the media and identity verification through a potentially compromised PGP key. Prior to AlphaBay, Alexander Cazes had a reputable history on the darknet – specifically in the carding community. A senior member from the carding community Ranklez claimed he had evidence to suggest Cazes wasn’t alpha02.
Yes, Maltego supports darknet plugins, allowing OSINT analysts to visualize and analyze relationships within dark web data. The most common tool is the Tor browser, sometimes used with a VPN for additional anonymity and protection. The MITRE ATT&CK framework provides a comprehensive view of adversary tactics. Singularity™ Threat Intelligence provides insights into adversary tactics and helps mitigate these risks before they impact your organization.
Other Government Sites
Cryptocurrencies such as Bitcoin have been the dark web currency even before they became available to the general public. Right now, you can use many cryptocurrency .onion sites to buy or sell all types of cryptocurrencies. While this is not much compared to standard email services, it is enough for PGP-encrypted messages. ProtonMail is a Swiss-based email service that is very easy to use.
Is It Illegal To Visit A Dark Web Site?
The creators assert that because their technique is so strong, even malware with root access could not determine the machine’s IP address. To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web. I2P, or the Invisible Internet Project, allows you to access the ordinary and dark web. Specifically, the I2P darknet is accessible, while the Tor network is accessible through the Orchid Outproxy Tor plugin. Initially, the dark web was mainly used by government agencies, big businesses, hackers, and cybercriminals. However, technological advancements such as encryption and privacy-focused browsers like Tor enabled the general public to access it.
During our tests for the research, we were able to register with a bogus email and a random username. All that one can expect from a deep web marketplace when it comes to anonymity and security. Track and analyze darknet activities using our advanced cyber threat intelligence platform to stay ahead of emerging threats. Archetyp Market was dismantled in June 2025 during Operation Deep Sentinel in a coordinated raid across six countries.