However, its network is still small, and there aren’t many hidden services available yet. By following these steps, you’ll have I2P and Hyphanet set up for secure and private browsing on the dark web. Both networks have unique strengths, and while they aren’t as user-friendly as Tor, they offer excellent alternatives for those seeking robust privacy and decentralized communication options. Hyphanet (formerly Freenet) is another anonymous network that allows you to share and retrieve information without censorship. It’s designed for secure, decentralized storage and is often used for file sharing and accessing information anonymously. It comes down to a threat-modeling exercise – evaluating vectors of risk then architecting layers of protection scaled appropriately.

Step 3: Install Tails On The USB Drive
Therefore, you need a specific dark web search engine known to provide top-notch security and privacy. The safer option of the security settings only disables the JavaScript on websites that aren’t “https” protected, while the safest option disables JavaScript on all websites. In contrast to the deep web, safely accessing the dark web is not as easy. The problem with the dark web is that, despite legal use, it also remains a hub of illicit activity. Therefore, while accessing dark web links, it is crucial to exercise immense caution.
- To help users decide whether premium tiers are worth it, here’s a comparison of free vs. premium features across engines like Haystak (and NotEvil’s free-only model for context).
- Some regions ban the Tor network entirely, such as China, Russia, and Iran, so check your country’s laws before using it.
- Stay informed about the latest security practices and developments related to the Dark Web.
- Be mindful of the activities you participate in to avoid legal consequences.
Opennet connections are easier to use, but darknet connections provide more security against attackers on the network. In darknet mode, you can select friends on the network and only connect and share dark web content with them. This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know.
Tools And Precautions
There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game. The major issue with these websites is that a whopping 50 percent are fake, and there’s no way of telling for sure if they’ll deliver or not. You should stay away from everything labeled “porn”, “card skimming services”, “PayPal hacks”, “firearms”, “real fake IDs and passports”.
Accessing The Dark Web On Various Devices
The best Android option is the Tor Browser, available on Google Play. For added privacy, use Orbot, which enables system-wide Tor routing for other apps. Severe vigilance and preparedness are needed to follow any footsteps here, from using a good VPN and secure browser to staying strictly anonymous. Thus, you will be able to explore the expanse of this depth without suffering from its heights of risk.
🛠️ Tools You Need To Access The Dark Web

Unlike Tor, however, it cannot be used to access the public internet. It can only be used to access hidden services specific to the I2P network. I2P cannot be used to access .onion sites because it is a completely separate network from Tor. Tor over VPN requires you to place some trust in your VPN provider but not your ISP, and is best if you want to access .onion websites.
- In 2025, I tested OnionLand for a dark web news aggregator for a media trends piece.
- Only click on trusted links and download files from reputable sources.
- Treat Hidden Wiki with caution and verify any link via multiple sources.
- For built-in Tor over VPN functionality, NordVPN operates specialized servers that automatically route you through the Tor network.
What Percentage Of The Internet Is Dark Web?
The Hidden Wiki is like a weathered map of the dark web—nostalgic, foundational, but incomplete. It’s my first stop when orienting myself in Tor, especially for quick access to trusted services like secure email or news sites. Its categorized structure saves time compared to random searches, but the outdated links and scam risks keep me on edge. Dark web search engines bridge this gap by crawling and indexing these hidden services, serving as the only way to navigate the Tor network’s uncharted terrain. They’re not just for cybercriminals—journalists use them to uncover corruption, researchers study subcultures, and privacy advocates dodge surveillance. In today’s increasingly interconnected digital landscape, proactive dark-web monitoring is no longer optional—it is a business imperative.
Use reputable antivirus or anti-malware software to protect against potential threats that may exist on the Dark Web. Regularly scan your system for any malicious software or vulnerabilities. Use common sense and trust your instincts when navigating the Dark Web.
AI-Powered OSINT Tools In 2025 How Artificial Intelligence Is Transf
Seek recommendations from reliable sources, such as trusted online communities or forums dedicated to privacy and security. Onion websites are websites that are only accessible through the Tor network. The “.onion” extension signifies that the website is hosted on the Dark Web and relies on the Tor network’s encryption and anonymity features to protect user identities. By following these steps, you can connect to the Tor network using the Tor Browser and start exploring the Dark Web with enhanced privacy and anonymity. Remember to exercise caution, adhere to ethical guidelines, and use the Tor network responsibly. The Tor network may slow down your internet connection due to the multi-layered encryption and routing.
These features are accessible from the Freenet interface under the “Community” and “Tools” sections. I2P (Invisible Internet Project) is an open-source network designed to allow anonymous and private communication. Although it’s not as widely used as Tor, I2P can provide robust anonymity and is well-suited for peer-to-peer file sharing. While Tor is the most common method for accessing the dark web, I2P and Hyphanet offer alternative options for secure and private browsing.
Mid-2010s: NotEvil And The Push For Moral Alternatives
The big downside is that your ISP will know you are using Tor, which is cause for concern in some places and will put many people off using this method. In this instance, too, it is important to use a logless VPN and pay with Bitcoin if you can to stay anonymous. The VPN over Tor technique is also susceptible to an end-to-end timing attack, though it’s highly unlikely.
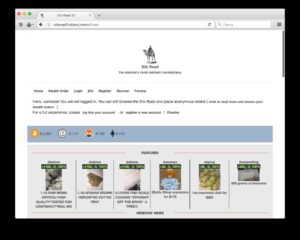
World Market Darknet
You cannot access the dark web using regular browsers like Chrome, Edge, or Safari. You must use a secure web browser that prioritizes privacy and security and can access onion sites. Even though it’s possible to access the dark web using incognito mode, this does not protect your online identity and activities.
What Are The Differences Between Ahmia And Torch As Dark Web Search Engines?
Its .onion link is bookmarked, but I use it cautiously, pairing it with Ahmia for safer searches. For newcomers or mobile users, it’s a solid entry point, but pros need to stay vigilant. OnionLand indexes both V2 and V3 .onion sites, as well as I2P content, offering versatility across dark web networks. However, its reliance on JavaScript for full functionality raises privacy concerns, as enabling it can expose users to tracking or deanonymization.