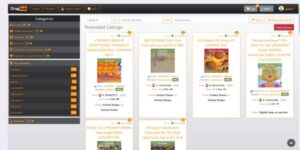
Finally, Google may not want content that appears on the dark web showing up in its search results. Kilos is a dark web marketplace search engine that lets users search for specific products they’re looking for. However, because Kilos is for the dark web, many of the items you may find may be unsafe or illegal.
Does Tor Hide Your IP Address?
And the search box can’t read certain characters like parentheses or quotation marks, which can be limiting. Even if you have good intentions, it’s easy to stray off the beaten path in the dark web and stumble onto illegal sites and materials. If you really do choose to visit the dark web, and have legitimate and legal reasons for doing so, it’s advisable to follow these security tips. Please remember that it’s not illegal to enter the dark web, but you browse there at your own risk and it’s your responsibility to abide by the law. With these criteria in mind, let’s dive into the top Tor search engines available today.
Navigating The Dark Web Safely
For added safety, consider using a VPN alongside the Tor browser to further protect your identity. The deep web is the part of the internet you can’t access through search engines like Google and Bing. Also referred to as “non-indexed” content, it’s any content hidden behind some kind of access control such as a log-in or code word. It contains 7,500 terabytes of information, compared with only 19 terabytes of information in the “surface” web. To look at it in a different way, it makes up between 90% and 95% of the internet.
The Web “iceberg” Has Three Layers: Surface, Dark, And Deep Web
BBC News is still around, though, along with a handful of others, ensuring that users can access impartial information, wherever they are in the world. The Hidden Wiki is one of the easiest ways to find useful resources and websites on the Dark Web. It is essentially a list of all the notable websites available on the Tor Network that is kept in a single, organized place. Although profiting from pirated copyrighted material is unethical and illegal, there are some exceptions to using copyrighted material, such as a “private study” provision under UK law.
The Importance Of Privacy And Security
- The process costs a fee, but unlike other “tumbler” or “mixing” services, there is no risk that Wasabi or any of its users could scam you out of your coins.
- Built-in features like script blocking and anti-tracking ensure a safer browsing experience.
- These domains are used for dark web sites seeking anonymity, where both the users’ and the providers’ identities are difficult to trace.
- In 2025, as privacy battles intensify, these tools are more vital than ever.
- This search engine’s indexing is relatively shallow compared to other uncensored engines, meaning many dark web sites remain undiscovered or unlisted.
Unlike many free tools, Haystak offers both a free version and a premium subscription. The premium service unlocks advanced features such as historical indexing, refined filters, and access to a larger collection of results. Among all the search engines available on the dark web, Ahmia stands out as one of the most trusted.
This means your ISP (internet service provider) won’t know you’re using Tor, and potential attackers on Tor can’t easily track your true IP address at vulnerable nodes. While operating similarly to its surface web counterparts, a dark web search engine is an online tool built to find .onion content hosted on the Tor network and ensure anonymity. These crawlers are designed to respect the network’s anonymity protocols and provide search results based on query keywords. A dark web search engine’s index is significantly smaller compared to the surface web due to its hidden nature. The dark web is a vast and often misunderstood part of the internet. While it houses a lot of illicit activity, it’s also a beacon for free speech, privacy advocates, and those looking for specialized information.
Newspaper
Some dark web search engines include a manual vetting process to ensure relevance and safety. Others integrate metadata extraction and ranking algorithms to determine a site’s trustworthiness or usefulness. For example, sites with high uptime or community upvotes may be prioritized in search results.
Bypassing The Lightspeed Systems Internet Filter: A Guide

These crawlers provide access to sites that cannot be accessed by normal search engines. The deep web includes all websites and pages that are not indexed by search engines and are not publicly accessible. The dark web changes quickly, and malicious sites remain a constant threat. That means combining these engines with strong browsing habits, using Tor with a VPN, and never downloading files from untrusted sources. Keeping your activity separate from personal accounts and devices also reduces risk exposure. But for the average user, it is not the best choice for safe exploration.
I2P comes with a router that connects you to the network and applications for communication and file sharing within the I2P ecosystem. If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web. You can also run a dark web scan to see if your information has been leaked on the dark web. This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks.
Over the years, technological advancements have transformed deep web search engines. The introduction of the Tor network revolutionized how you access the deep web. By enhancing user anonymity, Tor ensures that your identity remains protected while you browse. This feature is crucial for anyone exploring sensitive or private content. While you don’t need to log in to access any of the dark web links listed here, you can’t find them with a search engine like Google. The only way to access the dark web is by using the correct browser and knowing the URLs of the pages you want to visit.
The system is designed to provide enhanced security and privacy features. Its key features include kernel hardening, application firewall, package security, filesystem encryption, meta-proxy encryption, and binary integrity. The US Naval Research Laboratory developed The Onion Routing (Tor) project in the late 90s. A network browser gives you access to sites with the ‘.onion’ registry operator.
Related Content

Tracking can happen through IP leaks, browser vulnerabilities, or malicious exit nodes. To reduce this risk, use the Tor Browser properly, keep your software updated, avoid sharing personal information, and pair it with a reliable VPN. Following best practices for online anonymity helps, but staying cautious is essential since no method is completely foolproof. Haystack doesn’t track or store your search queries or personal data, which is critical to maintaining anonymity on the dark web. Dark Search has earned acclaim for its user-friendly interface and robust security measures.
How To Stay Safe On The Dark Web
SecureDrop is a site that protects the privacy of journalists and whistleblowers. Awazon became the successor of the popular AlphaBay market, which the authorities shut down successfully in July 2023. Like any other site of such nature, Awazon Market isn’t free from risks, so be careful while accessing it. This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. However, it has a sneak peek, easy guide steps, and/or a quick list providing quick in-page navigations and easily-found answers if desired. Password managers can help manage your credentials without compromising security.