Learn how darknet markets function and the challenges they present to cybersecurity, shedding light on the hidden side of the internet. Elysium Market brands itself as a “premium” marketplace, featuring exclusive vendors who undergo an intensive onboarding process. Known for its tight-knit community and high-value listings, Elysium favors privacy-oriented coins like Monero and employs a closed, invite-only system to limit access. This restricted membership model is meant to reduce scams and protect both buyers and sellers from external threats. The mirror network spans multiple geographic locations and hosting providers, ensuring that users can always find a reliable access point regardless of their location or local internet restrictions. All mirrors maintain the same high standards of security and functionality as the main platform.
Ares also has several mirrors that work separately from each other, and if some Ares onionmarket mirror does not work, you can try switching to another one. Buying illegal substances, stolen merchandise, and counterfeit currency or goods online poses significant risks for both the buyer and the seller. This market specialized in selling marijuana related products and magic mushrooms, with no “hard drugs” for sale. DNMs have a limited life and may be shutdown suddenly, leaving users with unfulfilled orders and sellers with no means of communication. Functionally, accessing DNMs and using them requires quite a few extra steps to protect the anonymity of the buyers, sellers, and server admins.
Accessing DNMs
This fusion of AI with illicit marketplaces could open the door to new forms of large-scale fraud, intensifying the cat-and-mouse game between cybercriminals and law enforcement. High-profile joint operations—like those targeting Silk Road, AlphaBay, or other major marketplaces—have demonstrated the potency of multinational task forces. Despite its name, Russian Market serves a global audience and primarily uses English for communication. It is known for its relatively affordable prices and diverse product offerings, which include RDP access credentials, stealer logs, and other cybercrime tools.

See Why DarkOwl Is The Leader In Darknet Data
- Since these platforms are less conspicuous than major marketplaces, they tend to survive longer under the radar of law enforcement.
- It is commendable to observe a market taking measures to enhance the overall user experience.
- They engage in financial crime and sell other people’s stolen personal information, since they’re under the veil of anonymity.
- Our arbitrators are trained in conflict resolution and maintain strict neutrality while applying consistent standards based on platform policies and transaction evidence.
- Ares Market has emerged as a standout darknet marketplace, boasting a strong community of over 500,000 registered users.
However, escrow transactions themselves may still provide opportunities for blockchain tracking according to some security researchers. Behrouz Parsarad (Parsarad), residing in Iran, was the sole administrator of Nemesis. In this capacity, Parsarad established Nemesis and held full control over the marketplace and its virtual currency wallets. Parsarad enriched himself from fees he charged users of Nemesis with every transaction, pocketing what OFAC estimates to be millions of dollars over the course of the marketplace’s existence. In addition to providing criminals with a platform to conduct transactions, Parsarad laundered virtual currencies for narcotics traffickers and cybercriminals active on Nemesis. Parsarad is charged with conspiracy to distribute controlled substances and distribution of controlled substances in the Northern District of Ohio and elsewhere.
- The markets often share materials related to child exploitation, pornography, and non-consensual recordings, all of which are serious crimes that inflict lasting harm on real-life victims.
- The Russian Market isn’t exclusive to Russian-speaking clients.
- If you think the Dark web marketplaces are just online shops, you’re wrong — these sites are the actual weapon stores for criminals.
- These features combine to make Ares one of the most secure and user-friendly darknet marketplaces available today.
- Activists, journalists, and whistleblowers use the dark web to communicate safely without fear of retribution.
Related Articles From The Business Security Section
Orders auto-finalize after 21 days if no dispute is filed, ensuring a balanced and secure trade environment. Every purchase requires payment to a unique, per-order address. This direct model reduces risks, speeds up payments, and preserves user autonomy. In order to conduct a more sophisticated search, it is necessary to perform a preliminary basic search. Subsequently, on the results page, you will be presented with the option to apply supplementary filters.
How Does Escrow Work For Digital Listings?

Depending on jurisdiction, charges can range from possession of illegal substances to conspiracy and money laundering. Law enforcement increasingly focuses on large-quantity purchasers and those seeking especially dangerous products, such as firearms or specialized hacking tools. Even smaller transactions can trigger investigations, given the international coordination among agencies targeting the dark web. Consequently, anyone participating in these markets faces the dual risk of financial and legal jeopardy. Darknet marketplaces face numerous challenges that can lead to their shutdown. Law enforcement raids represent one of the most common causes, as coordinated international operations often target servers, seize assets, and arrest site operators.
Advanced Escrow
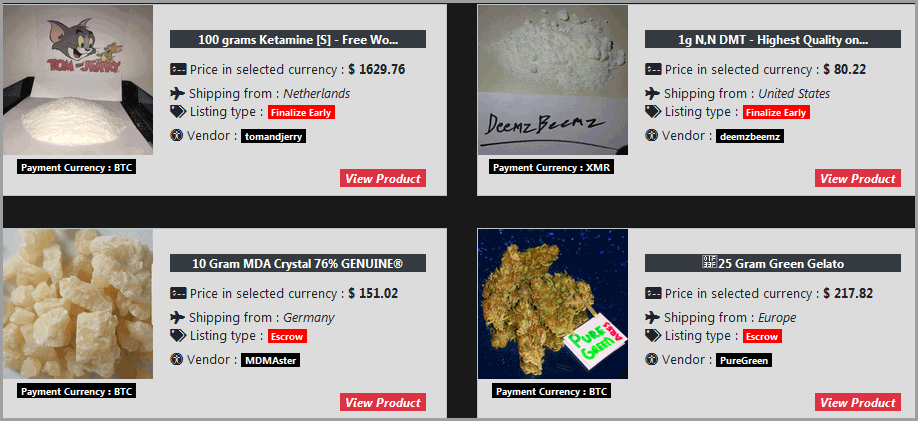
Here you are presented with a wide selection of various drugs, as well as digital goods. There are quite standard restrictions for darknet markets, such as “no weapons”, “no child porn”. Darknet marketplaces in 2025 illustrate a resilient and evolving underground economy.
Abacus relies on robust escrow services, vendor rating systems, and multiple cryptocurrency payment options to streamline transactions and maintain a degree of trust among its user base. Significant technological innovations and trends have reshaped dark-web marketplaces over recent years. In 2025, many platforms have adopted decentralized architectures, reducing single points of failure that previously made them vulnerable to law enforcement takedowns.
Is There A Future For Dark Web Marketplaces?
This is an estimated reading time to let you know how long it will take you to read all the content on this particular PrivacySavvy.com page. However, it has a sneak peek, easy guide steps, and/or a quick list providing quick in-page navigations and easily-found answers if desired. Distributed infrastructure with DDoS protection and advanced threat detection.
Fraudsters create fake versions of popular darknet sites to trick users into entering login details or personal data. If you fall for it and log in, they immediately steal your credentials and either sell or use them for other scams. As we mentioned earlier, not everything sold on dark web markets is illegal. As terrible as its reputation may be, some vendors sell legitimate goods or services. Some customers even use the dark web to make anonymous purchases, especially in areas where privacy is a huge concern. So, not everyone who shops there is looking for something illegal.

End-to-End Encryption
Finally, an “exit scam” can occur when marketplace operators abruptly shut down the site, absconding with user funds held in escrow, leaving buyers and vendors at a loss. Operational security (OPSEC) extends to how marketplaces and forums vet newcomers and moderate ongoing transactions. Moderators often request proofs of credibility, such as verified PGP signatures, to ensure participants are not infiltrators or scammers.
This transparency allows buyers to make informed decisions while incentivizing vendors to maintain high standards and excellent customer service. The security layer incorporates multiple protection mechanisms including anti-phishing measures, DDoS protection, and advanced encryption for all user data and communications. Our security team continuously monitors for threats and implements proactive measures to protect user privacy and platform integrity.



