This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to. Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. The advantage of using a dedicated computer just to browse the dark web is that your main computer isn’t exposed to any of the threats or risks tied to entering the dark web. In case of an attack, you can be sure that any of the data or information stored on your main computer will be safe. Government cyber teams can take such websites down, arrest the owners and then use the website to track and follow users that show activity on the website.
New Shamos Malware On Mac: Beware Of ClickFix Attacks
The dark web is also a place for scammers to attract vulnerable and unwitting victims. The platform is also used by governmental cyber departments to identify and track potential criminals or offenders. You can never be sure who’s really behind the other end of the line. Unfortunately, it’s also a place where the bad guys can offer their services – for example, hackers or hitmen.
These attacks often include stealing victims’ data and threatening to release it on the dark web if the ransom isn’t paid. This information can be used to target ads and monitor your internet usage. Also, there’s a vast amount of unsavory content on the dark web, as well as a significantly high number of hackers and scammers looming on the platform. Simply accessing the dark web and using the Tor browser may already raise government suspicion. Keep in mind what you’re looking for, find that information, and disconnect from the dark web.

Dark Web Links – Darknet Markets Darknet Market Links In 2025
- In addition to its emphasis on stolen credentials, 2easy Market offers a variety of cybercrime tools, such as hacking services, exploit kits, and other resources for conducting cyberattacks.
- Journalists in overly restrictive countries also appreciate the anonymity of the dark web.
- Axis Intelligence provides dark web surveillance solutions that help businesses identify leaked credentials, fraud attempts, and malware risks before they escalate.
- At BLACKOPS’s core lies a steel lattice of technology—Tor cloaks every step, Monero buries every coin trail, and PGP seals every pact in unbreakable cipher.
The dark web is only accessible through specific software like Tor (The Onion Router). Also, while this huge portion of the internet has a reputation as home to nefarious activities like hacking and drug trafficking, it also harbors legitimate activities like journalists and whistleblowers. In May 2024, Ticketmaster faced a significant data breach affecting millions of customers.

Tips To Stay Safe When Using The Dark Web

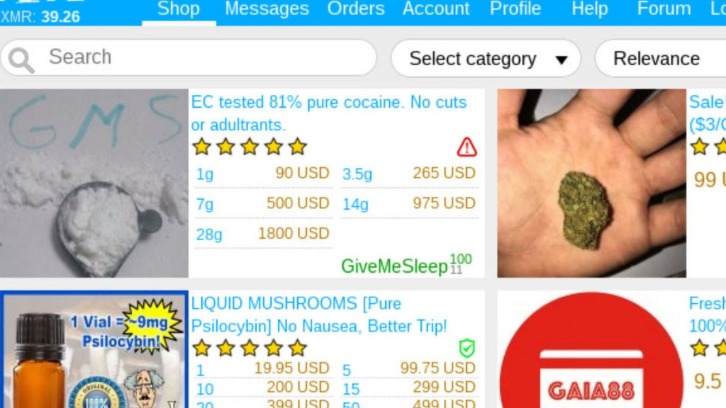
They usually accept cryptocurrencies, such as Bitcoin, which keeps transactions secret. There are no visible ads or trackers, and the design is often very simple. For faster transactions and trusted vendors, our 7-day escrow option provides quicker fund release while maintaining security. This option is ideal for digital products, domestic shipping, and transactions with established, high-reputation vendors. The most recent example is the shutdown of the oldest marketplace Hydra Market in 2022 which took a combined effort of the FBI and the German authorities.
Torzon Market
Therefore, you can prevent this exploitation by setting up a non-admin account. We recommend you only visit safe dark web links to explore such as The CIA, Facebook, DuckDuckGo, and Torch. Some services are genuine; you can get what you want at an agreed fee.
Doing so makes it harder for authorities to identify who’s behind a purchase or a listing. Vendors often build up reputations through ratings and reviews, just like sellers on mainstream platforms. To reduce scams, many markets also use escrow systems, where the site holds the buyer’s payment until they confirm the item has been delivered. As a rising authority in the BlackOps darknet landscape, the marketplace enforces rigorous security measures including mandatory PGP encryption, multi-signature escrow, and thorough vendor verification. This creates a curated, premium environment that distinguishes BlackOps from larger, less secure alternatives. Accessing the BlackOps market website through a trusted BlackOps market onion link guarantees authentic interaction with the official resource—not a counterfeit or compromised copy.
Payment Methods Overview
The dark web news site Deep.Dot.Web teems with stories of buyers who have been arrested or jailed for attempted purchases. The dark web has flourished thanks to bitcoin, the crypto-currency that enables two parties to conduct a trusted transaction without knowing each other’s identity. “Bitcoin has been a major factor in the growth of the dark web, and the dark web has been a big factor in the growth of bitcoin,” says Tiquet. There are also many tools that can be use to monitor the dark web and scan for personally identifiable information and even respond to attacks. It offers outstanding privacy features and there is currently a discounted rate available through this link. Anyone can access the dark web, and it’s not that complicated to do so.
Other Government Sites
While it’s true that it hosts illegal activities, it’s also a haven for those seeking privacy from prying eyes. Activists, journalists, and whistleblowers use the dark web to communicate safely without fear of retribution. The term “dark” doesn’t necessarily mean illegal; it simply indicates a layer of the internet not indexed by conventional search engines.
There’s high exposure to malware and cybersecurity threats that can steal your personal information. Law enforcement agencies actively monitor these markets and can track users despite anonymity measures. You risk legal consequences if caught participating in illegal transactions.

It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals. Overall, Subgraph OS is a secure and privacy-focused operating system well-suited for high-risk environments. Additionally, you can opt for Subgraph OS as a second option to Tor. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. An easy way to find content on the dark web is to receive a link from someone who already knows about it.
Our escrow system ensures that both buyers and vendors are protected throughout the entire transaction process. Black Ops Market exclusively supports Monero (XMR) transactions to provide enhanced privacy and true anonymity for all users. Unlike Bitcoin and other cryptocurrencies that leave traceable transaction records on public blockchains, Monero offers genuine privacy protection through advanced cryptographic techniques.
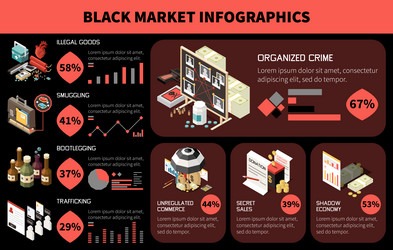
As law enforcement agencies’ tactics improve, some markets respond by introducing more security features, like mandatory encryption or invite-only access. But no matter how polished or professional these sites seem, the risk of getting scammed — or tracked — is always high. Most buyers and sellers use the Tor network, which hides IP addresses and locations.
- Such data includes medical records, financial information, research papers, private forums and networks, and other content.
- Many “trusted” sellers use fake reviews or steal reputations from shutdown markets.
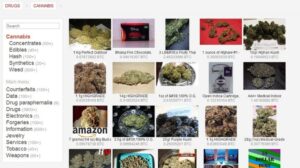
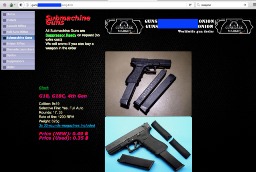
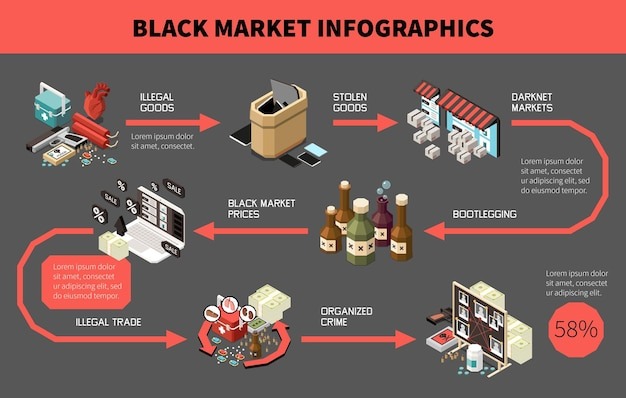
- On the other hand, it’s notorious for enabling illegal activity, including drug sales, weapons trafficking, counterfeit ID trading, hacking services, and the exchange of stolen personal data.
- Discover how to safely access dark web marketplace links while ensuring your privacy and security online.
- The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose.
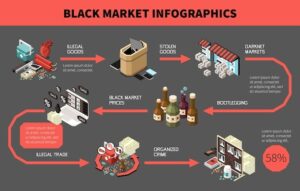
Some believe STYX is the OG darknet market when it comes to financial crimes. It trades in hacked bank accounts, stolen credit card information, and other services that facilitate cryptocurrency laundering. Deep web marketplaces are online marketplaces where people can buy and sell illicit goods and services under the protection of the anonymity of the dark web.