This double encryption also protects against compromised Tor entry nodes that could potentially monitor your activity. Wherever you go online, but especially if you’re on dark web websites, using a VPN helps you secure your communication data and protect personal information you send or receive. Avast SecureLine VPN encrypts all of your internet traffic to help block hackers and keep snoops out.
How Do I Access Onion Sites?
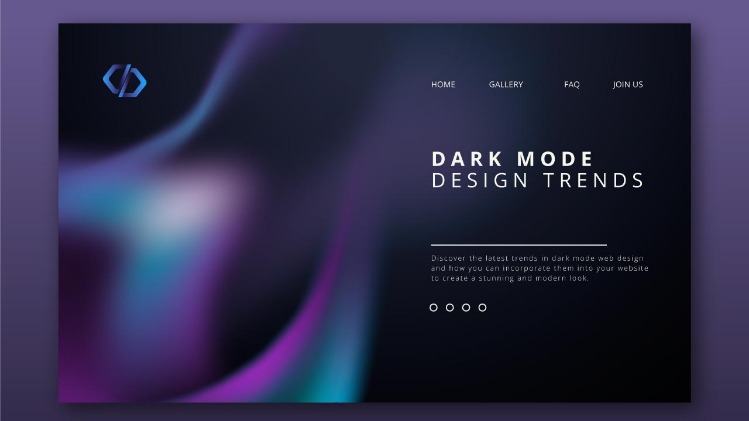
However, the same anonymity also facilitates illegal activities, including data breaches and unauthorized sales. Businesses are encouraged to conduct regular cybersecurity risk assessments to prevent their data from being traded on the dark web. The surface web is the most familiar layer, comprising websites indexed by search engines like Google or Bing. This layer includes publicly accessible platforms such as news websites, e-commerce stores, and social media. As when visiting ordinary websites, stay alert to security risks on onion sites. Don’t click on suspicious links, be skeptical of what you read, and avoid dark web marketplaces if you don’t want to stumble on illegal activity or content.

Should I Use Services Like Web2Tor?
There are often copious amounts of how-to articles, software exploits, and hacked credentials for sale. Not every visitor is a criminal, but this is where most cybercrimes begin. Some markets even sell privacy tools, but you are more likely to run across counterfeit prescription pills and stolen identities. These are the primary sources of what the general public thinks of as “dark web.” Online marketplaces selling hacked credit cards, fake passports, malware kits, untraceable drugs, anything. It has a feature called CoinJoin that combines multiple coins from different users into a single transaction.
More On How To Stay Safe On The Dark Web
Tor anonymity comes with a cost since malicious hackers and criminals like to operate in the shadows. For example, perpetrators of trafficking and cyber attacks use the dark web to disguise their actions. Therefore, the legality of the dark web will mainly depend on how you use it.
Using Tails OS can further security, as all your data is reset every time you close the device. Pitch is a dark web-based Twitter/X alternative, providing a secure platform for anonymous discussions and information sharing. Unlike many dark web platforms, it maintains strict content guidelines while protecting user privacy. Alt Address provides disposable email addresses specifically designed for dark web use.
ProPublica is an investigative news site owned by an independent nonprofit that exposes abuses of power and corruption. It hosts an onion site so people in countries with restricted press freedom can access its journalism, which covers everything from hacktivism to government repression. The CIA’s onion site allows users to securely report threats or suspicious activity, especially in regions where online surveillance is common. Its presence on the dark web also supports intelligence gathering and helps track cybercriminal activity. But despite its many benefits, it’s sadly just a matter of fact that the dark web can be a dangerous place.
Illegal Activities On The Dark Web
To access the dark web safely, you will need the Tor browser as it allows you to navigate .onion sites. Additionally, using a VPN like Forest VPN is highly recommended to protect your identity and encrypt your internet traffic. Before you venture into the dark web, it’s crucial to secure your privacy with a reliable VPN like Forest VPN. Forest VPN provides an additional layer of encryption and masks your IP address, preventing your internet service provider (ISP) and other entities from tracking your online activities.
Legitimate Use Cases For The Average User
Journalists in overly restrictive countries also appreciate the anonymity of the dark web. The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose. That means that only 0.024% of all the known pages are findable in Google’s search engine. The users only have access to a fraction of the available data and web pages.
If you make use of a password manager, then it may come with a feature that monitors the dark web for mentions of your email address and password, or any other personal details. It’s something built into the password management services offered by Apple and Google as well, so you don’t need to trawl through data leaks manually yourself. Sections of the dark web are often closed down too, as part of police operations. Even with Tor and onion routing in place though, you’re not suddenly completely invisible and free to do whatever you want, without repercussions. Certain details of your traffic can be intercepted at the entry and exit points of the node, by the people running those nodes, if they know what they’re doing and what they’re looking for.
Best Dark Web Links
The search engine has indexed over 400,000 pages, and you can ask it to match your exact search term. You can easily find what you are looking for, even links to hidden dark web rooms. With its nifty “conjoin” feature, users can combine different coins in one transaction, covering the user’s tracks and maintaining their anonymity. The wallet is user-friendly and provides robust security, making it one of the best crypto wallets on the dark web.
- You can archive any site you want, or retrieve historical records wherever available.
- If you need to access dark web resources, these are the steps you need to take.
- But if you must visit the dark web for ethical reasons, here are some safety precautions.
- To access the Freenet-based dark web, you need to install the Freenet application.
- For example, the Freedom of Information Foundation has long advocated for the use of the Dark Web in enabling free speech in repressive regimes.
- While you don’t need to log in to access any of the dark web links listed here, you can’t find them with a search engine like Google.
Torch is one of the oldest dark web search engines, having served the darknet community for years. It boasts a vast archive of over 400,000 pages, providing comprehensive coverage of .onion sites, including forums, blogs, and marketplaces. The dark web is a part of the internet that isn’t indexed by traditional search engines like Google. It requires special software to access, with the Tor browser being the most popular choice. This network is characterized by its focus on privacy and anonymity, making it a haven for those who prioritize these values, including journalists, whistleblowers, and privacy enthusiasts.
Install And Update Security Software
As a result, we want you to stay safe and anonymous by using a paid VPN service whenever you surf this dark web platform. OnionLinks is a library of dark web links, most importantly, active links. Depending on your preference, you can find links in well-categorized groups. These categories include email providers, news sites, privacy, and commercial services. Their website is accessible on the clear web, but it also has a .onion site, allowing visitors to browse it anonymously, especially those living under oppressive regimes.
People like spies or whistleblowers often contact the CIA via the dark web to keep themselves hidden. But we are on the dark web, you can’t trust anyone, so there may be sites containing illicit content. You must review the site’s descriptions before you click to open them.
Popular Dark Web Search Engines: An Overview Of Ahmia, DuckDuckGo onion, Torch, And Not Evil
You should only ever access websites you know are safe because they’re vetted by websites or other sources that you already know are safe. Take a look at the sites that these directories have collected and see what topics interest you. These sites are intentionally hidden to protect the privacy and anonymity of both the site operators and visitors. The dark web consists of websites that use encrypted .onion domains, which require specific software and protocols to access. The dark web itself is not illegal, but many activities conducted there are. If used responsibly, it serves as a valuable tool for privacy, free speech, and secure communication.