One of the most concerning aspects of the dark web is the prevalence of illegal activities. Users may inadvertently encounter illicit content, such as child exploitation materials, counterfeit documents, or illegal drug marketplaces. Even browsing such content, intentionally or not, can have severe legal ramifications in many jurisdictions.
Continue Reading About What Is The Dark Web (darknet)?

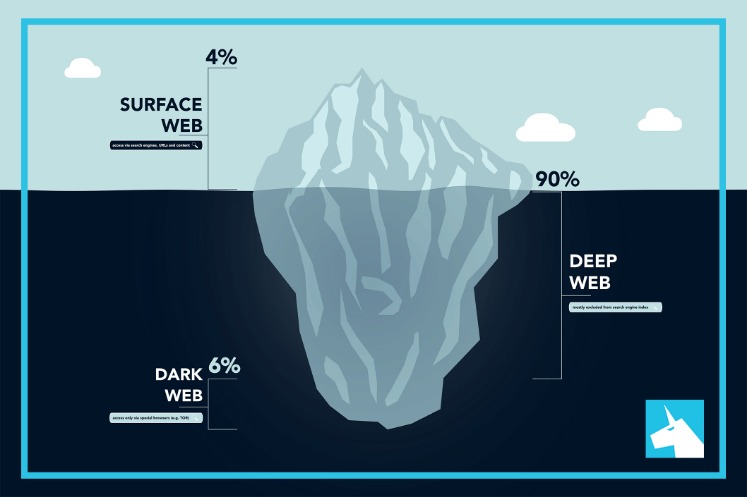
Though no one should bat an eye just because you’re attempting to access the dark web, keep in mind that in some countries, like the United States, even a simple foray can get you in trouble. It makes up about 6% of the internet, and it’s where you find everything from illegal marketplaces to forums for whistleblowers. Hackers spend a lot of time on the dark web, and it’s not too difficult to get access to hacking tools and data leaks in this part of the internet. However, it’s much harder to get at the people who are doing the uploading and downloading.
What To Do If You See Something Illegal
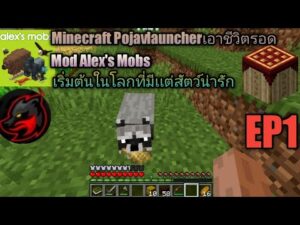
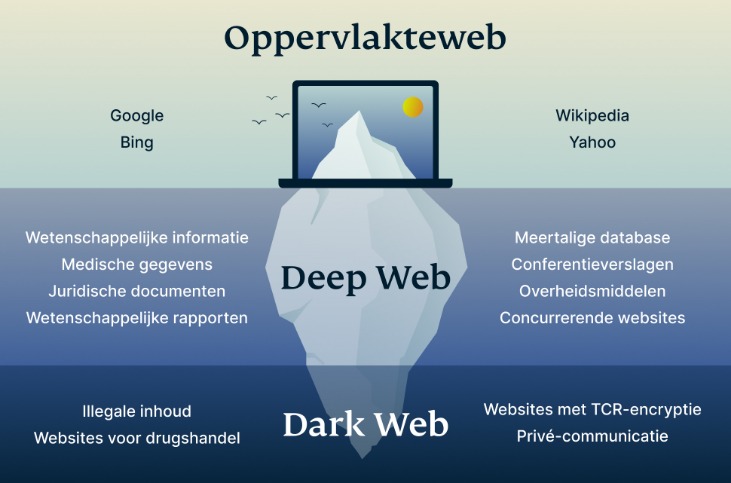
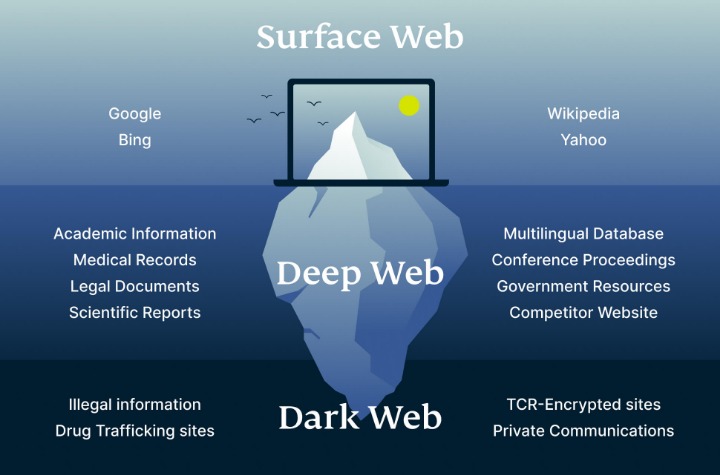
For some users, portions of the deep web offer the opportunity to bypass local restrictions and access TV or movie services that may not be available in their local areas. Others go somewhat deeper to download pirated music or steal movies that aren’t yet in theaters. The Internet is sizable with millions of web pages, databases, and servers all run 24 hours a day. But the so-called “visible” Internet (aka surface web or open web) — sites that can be found using search engines like Google and Yahoo — is just the tip of the iceberg. First and foremost, it\’s crucial to use the Tor browser, renowned for its privacy features.
Legal Activities
However, DuckDuckGo doesn’t index dark web content — it only accesses surface and deep web sites through Tor. Engaging in illegal activities on the Dark Web, such as buying illicit drugs or participating in hacking forums, can lead to serious legal consequences. Law enforcement agencies around the world actively monitor the Dark Web for illegal activities, and many criminals have been caught and prosecuted as a result of their actions online. Even if users maintain their anonymity, they are not immune from detection. The Dark Web refers to a specific section of the internet that exists on an encrypted network, intentionally hidden and accessible only through specialized software.
Encrypted Communication Tools
Though it is not illegal to visit the dark web, accessing it can expose you to serious legal risks, even if you don’t have any criminal activity in mind. Suppose you share your name, social security number, or any other personally identifiable information on any dark website. In that case, there is a high chance that your data will become accessible to cybercriminals. Then, they can use your data to impersonate you and run social engineering attacks to target your loved ones. However, with the right security measures and cautious browsing, you can minimize these dangers.
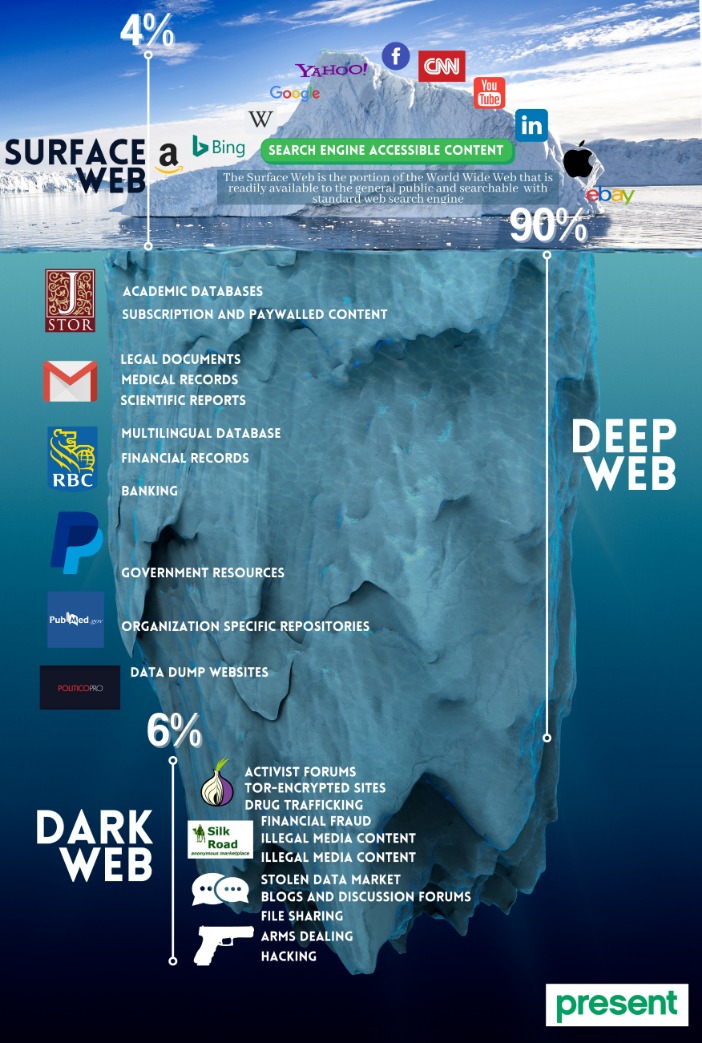
It is often offered in some portals to give threat actors the tools for cyberattacks. However, it also lingers all across the dark web to infect unsuspecting users just like it does on the rest of the web. In case you’re wondering how to access the deep web, chances are you already use it daily. The term “deep web” refers to all web pages that that are unidentifiable by search engines. Deep web sites may be concealed behind passwords or other security walls, while others simply tell search engines to not “crawl” them.
How The Dark Web Works

“It’s a live reconnaissance zone,” says Ensar Seker, CISO at SOCRadar. Threat actors target organizations based on exposed credentials, stale access points, or misconfigured assets advertised or sold. A lot of this information is inexpensive and readily available — opening the door to attacks. Each warning for data leaks also includes the type of information exposed and the essential steps to limit your exposure.
Is It Illegal To Go On The Dark Web?
Dark web websites won’t show up on Google, but they are indexed by dark web search engines such as Torch. The biggest and most frustrating part about dark websites is that they live for a short span of time. These platforms keep changing their addresses to avoid DDoS attacks or law enforcement agencies. Talking about copycats and potential risks, due to its high risk and low signal-to-noise ratio for legitimate content, we advise beginners and privacy-conscious users to avoid The Hidden Wiki. If you must explore sites like The Hidden Wiki, do so with extreme skepticism, never download files, never enter personal info, and never send cryptocurrency to unknown sites.
That said, many of the actors on the dark web are highly skilled digital adversaries who can easily outmaneuver basic security measures. As a leading cybersecurity vendor, CrowdStrike cautions all organizations and individuals to refrain from using the dark web. The dark web contains a wide variety of services and content, some of which skirts or disregards legality. Though the intention and purpose of users on the dark web may vary, the dark web itself is neither good nor bad. The dark web continues to be a valuable tool and exchange network for many groups around the world. Some consider it an outright necessity, as it helps encourage free speech, maintain a free press, and support the work of law enforcement and government agencies.
The Hidden Wiki
Tor has a 3 layer proxy node structure, like the layers of an onion (hence the onion sites!). All of your web page requests on the Dark Web are first connected at random to one of the entry nodes, then bounced off a middle node, and then finally pushed out through an exit node. This makes your IP address unidentifiable and untraceable so you might be sitting in India but you may appear to be in a country halfway around the globe on the Dark Web! This makes Tor perfect to explore the secret Dark Web but also makes it a little unpredictable and slow due to all the onion layers. Even unintentional exposure to illegal content can have serious repercussions.
- “Identity fraud is enhanced through synthetic persona generation and deepfakes, aiding criminals in bypassing know your customer (KYC) and biometric checks,” says Kroll’s Currie.
- To prevent detection, the program runs user data via a tiered stream before allowing access to the dark web.
- The dark web comes with its own set of tools and services, including web browsers and search engines (which I’ll get on to in a moment).
- It’s also used by journalists, advocacy group members, and political refugees in hiding.
- Additionally, it’s recommended to disable scripts and plugins to minimize vulnerabilities.
- These sites offer access to illegal streaming of pirated movies, TV shows, sports events, or other copyrighted content, often in high quality.
- You can check our guide on the best VPN services to find the right VPN solution to protect your privacy.
- Staying aware of what’s happening on the dark web is key to improving digital safety.
- The deep web also includes most academic content handled directly by universities.
- Unfortunately, it requires you to have an invitation code to create an account.
In addition, the dark web can’t be accessed through typical browsers such as Firefox or Chrome. It can only be accessed through an encrypted peer-to-peer network connection or by using an overlay network, such as the Tor browser. The browser is free to download and use, and works with all major operating systems. In addition to the Tor browser, users can further protect their identities when accessing the dark web by doing so through a virtual private network (VPN). The dark web is an encrypted portion of the internet not visible to the general public via a traditional search engine such as Google. Also known as the darknet, the dark web constitutes a large part of illegal activity on the internet.
If you live in the EU and want to know what data your provider has collected about you, the GDPR gives you the right to request a full report. However, it is often prohibited for ISPs to sell your data to third parties. With all this data, your ISP could create a very accurate profile of you and link it to your IP address.