
The Dark Web—a hidden part of the internet accessible only through specialized software like Tor—has become increasingly significant as we enter 2025. Welcome to our definitive guide on the top anonymous and secure online stores. In this article, we’ll explore the world of fish market url and darknet markets shopping, uncovering the safest and most reliable platforms to fulfill your needs. Whether you’re seeking privacy, enhanced security, or simply a seamless shopping experience, we’ve got you covered. Join us as we delve into the latest trends and innovations in the world of anonymous and secure e-commerce. It was quite popular for selling a wide range of products and services.
Buyers benefit from PGP-encrypted communication, preventing third-party interception. The use of Tor and onion routing further obscures user activity, maintaining privacy throughout the transaction process. Vendor profiles on Nexus display detailed transaction histories and customer reviews, enabling informed purchasing decisions.
Reputation
These listings often include detailed descriptions, user reviews, and even shipping guarantees. Even if you’ve never visited these markets, your personal and financial data might already be there, having been leaked through a data breach. Criminals use this information for money laundering, opening bank accounts, applying for loans, and draining your finances.
Encryption And Security
Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data. A 10-month investigation following the closure of the dark web’s largest illegal marketplace, DarkMarket, has resulted in the arrest of 150 suspected drug vendors and buyers. We do not engage with darknet markets; our mission is exclusively dedicated to providing information for research and educational purposes. With every action encrypted and every identity compartmentalized, users step into a framework where operational security is not a feature — it’s the foundation. Law enforcement shutdowns are also only one type of disruption that dark web communities face. To access darknets, users typically need to download and configure the Tor Browser; a modified version of Mozilla Firefox that routes all traffic through the Tor network.
While some transactions involve illicit goods and services, these platforms also host a diverse range of legal and unique digital products that cater to specific audiences. Empire Market is a dark web shop that resembles the AlphaBay marketplace. Its look, design, options, and interface are exactly the exact copy of its competitor, but everything else, including buyers, vendors, and servers, is different. At its launch, the platform accepted payments through Litecoin, but now it has incorporated support for other payment methods like Monero and Bitcoin. The platform also cares about its users and uses PGP encryption and two-factor authentication to secure their data and communication. Its intuitive interface and advanced search features make it easy to find local and global products.
Dangerous Fake Or Malicious Vendors
Darknets are not limited to criminal activities; nation-state actors use these hidden platforms for espionage, disseminating propaganda, and recruiting agents. The significance lies in the potential compromise of national security. Governments and businesses must invest in advanced threat intelligence, cyber defense, and counter-espionage measures.
The Top 7 Dark Web Marketplaces In 2025
These search engines neither track your search queries nor record any information, improving digital privacy and keeping your data private. Using a dark web search engine is a great step towards enjoying a more secure experience while shopping on the platform. Not all marketplaces you want to visit can be accessed through regular search engines. In addition, mainstream search engines also track your searches and collect personal information. DarkOde Reborn is a great darknet market where you can find anything you want.

The 17 Best Dark Web Marketplaces In 2025
But since its relaunch, the developers are focusing more on operational security and ensuring that users can have a good experience on this site. The White House market offers impressive features like a mandatory PGP requirement that enables 2FA for the user’s profile and adds a protective layer. The browser uses onion routing technology to route the internet traffic through multiple relay nodes that provide layered encryption. The layers of encryption hide your data and activity from snooping eyes.

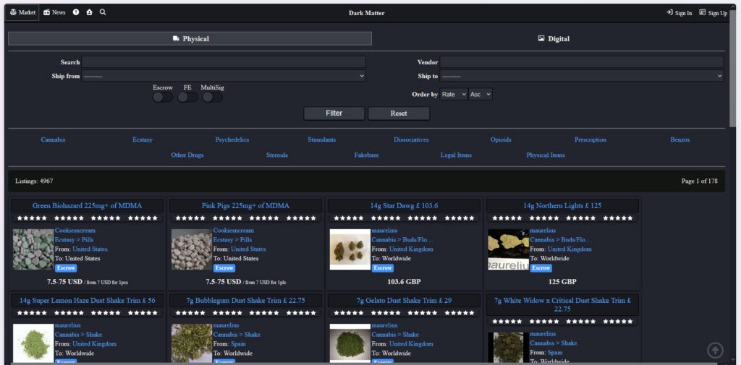
Dark Matter Marketplace

Of course, the promise of secrecy and unfiltered access might lure you in, but those same features are what make the environment so risky. Just like on the regular internet, phishing is a big problem on the dark web as well. Fraudsters create fake versions of popular darknet sites to trick users into entering login details or personal data. If you fall for it and log in, they immediately steal your credentials and either sell or use them for other scams. This can include everything from full names, email logins, and passwords to credit card details, social security numbers, and bank account information. The cybercriminals trade even sensitive documents, such as medical records, passport information, and driver’s licenses.
The Hidden Economy: Navigating The Underbelly Of Closed Darknet Marketplaces
Learn how to automate financial risk reports using AI and news data with this guide for product managers, featuring tools from Webz.io and OpenAI. STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity. To turn it on, just go to the “Settings” and then the “Tools” section of the NordVPN app and activate “Dark Web Monitoring.” In the end, it’s all about staying one step ahead. The more proactive you are, the better you can protect yourself against identity theft and other cyber threats. They’re tightening security and carefully screening anyone who wants to join. This vetting process helps keep the community “clean” from spies, law enforcement, or anyone who might pose a risk.
So, if a “business opportunity” sounds too perfect, it probably is. Surprisingly, most guns on the darknet actually start as legal products. The UNODC (United Nations Office on Drugs and Crime) maintains that almost all firearms are originally manufactured through legal means. Purchases through links on our pages may yield affiliate revenue for us.
- The goal is simple — make financial fraud easy and get as much attention as possible.
- We’re constantly exploring new ideas and pushing the boundaries of torzon mirror technology to create innovative solutions that revolutionize the torzon darknet industry.
- It supports operations in multiple languages and operates on both clearnet and Tor.
- Each product is accompanied by detailed descriptions and reviews, which greatly simplifies the selection and purchase process.
Its interface is characterised by simplicity and convenience, which has earned it high marks from users in numerous surveys… There are a lot of misconceptions about the dark web online and in popular media. When most people refer to the dark web, they are thinking about dark web/darknet marketplaces (DNMs). The dark matter shop provides detailed educational materials and dark matter tor access tutorials for new participants.
While hiring a hacker might sound like something out of a movie, it’s a very real threat. Businesses may use these services to sabotage their competitors, while individuals may seek revenge or simply want access to private information about someone. Understandably, as in the case with most illicit trade markets, you don’t even need to verify your email Awazon. Active for a decade since 2014, it is a widely used credit card shop used to source stolen credit card information such as dumps, CVVs, Wholesale Accounts. As of 2020, nearly 57% of the dark web was estimated to contain illegal content, including violence and extremist platforms. Vendors on these platforms employ stealth shipping techniques, masking package origins and contents.



