
Radar Rundown The dark web consists of many websites with uncensored information; choose a suitable … There are several other browsers you can use, such as Freenet and I2P, but Tor is the most recommended option. Unfortunately, the platform was shut down in 2013 after an extensive investigation that was spearheaded by US Senator Charles Schumer. The closure led to the arrest of the platform’s founder Ross Ulbricht. According to the United Nations Office on Drugs and Crime (UNODC), all guns are manufactured legally. Therefore, it means that even the guns on the dark web start legally, but along the way from creation to purchasing, a lot of things happen, which makes it easier for the guns to end up on the dark market.
There’s a significant risk to dark web users of being exposed to malware (malicious software) infections. There are several programs that hackers frequently use on the dark web. Unfortunately, it’s also a place where the bad guys can offer their services – for example, hackers or hitmen. Due to its absolute anonymity for knowledgeable users, the chance of running into bad people is also realistic, as they can operate relatively freely without the fear of getting caught doing something unlawful. Opennet connections are easier to use, but darknet connections provide more security against attackers on the network.
Explore Dark Web Marketplace Links With Confidence

It is important to note that engaging in such activities is illegal and unethical. The financial repercussions for victims can be debilitating, leading to damaged credit scores, fraudulent charges, and identity theft. Furthermore, participating in these illegal activities carries the constant risk of being caught by law enforcement agencies. However, delving into the Dark Web comes with significant risks and challenges. Buyers must navigate through a labyrinth of fraudulent sellers and law enforcement operations targeting illegal marketplaces.
Using TAILS is yet another security measure that protects your online identity on the dark web. It is a specific Debian-based version of Linux software that leaves no traces of the user activity or the operating system on the computer. It uses the Tor network because it is a popular network that helps to circumvent censorship and online surveillance.
Step 3: Fund Your Darknet Wallet
But again, your ISP won’t be able to see any of the content you’re reading or what you are sending and receiving through the Tor network. The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as “.onion”, which means that the URLs are only accessible by Tor users. It has been estimated that a large percentage of dark web traffic is related to illegal pornography that includes underage victims. Business operational data, such as operational data, financial data, intellectual property, and trade secrets can be found on the dark web.

Biggest Dark Web Marketplaces
While the dark web is not exclusively dedicated to illegal transactions, it cannot be denied that a significant portion of the activities that occur on this hidden network involve illicit goods and services. The anonymity and encryption offered by the dark web make it an attractive platform for cybercriminals and individuals seeking to engage in illegal activities. Account sellers on the dark web exploit various methods to obtain or create gaming accounts, including hacking, phishing, or using stolen payment information to purchase games or in-game items. These illicit activities compromise the security and integrity of gaming platforms, leading to frustrations for both game developers and legitimate players. The dark web is a notorious marketplace for the sale and trade of login credentials of popular websites. These credentials can include usernames, email addresses, and passwords, allowing cybercriminals to gain unauthorized access to online accounts.
Dark Web Marketplace Links
A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. It’s a precaution to protect yourself before diving into the dark web. For recommendations on choosing a VPN, look for expert reviews and articles. Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny. The US Supreme Court has indicated that even casual browsing could lead to legal consequences. Privacy and anonymity are the dark web’s hallmarks, thanks to a network of servers that hide users’ identities and locations.
How Much Is Stolen Data Sold For On Darknet Markets?
Even after Silk Road went down, dark web marketplaces haven’t slowed down. Stopping their growth takes serious effort from US agencies like the FBI, often working hand-in-hand with international law enforcement. If you take a quick look through darknet marketplaces, you’ll instantly notice an overwhelming supply of pirated content. We’re talking about even early access to unreleased music, leaked TV episodes, concert footage, and even popular video games before they officially drop.
The Dark Web, often mistakenly referred to as the Deep Web, is a clandestine part of the internet that is not indexed by traditional search engines like Google or Bing. It exists on encrypted networks, such as Tor (The Onion Router), which offer users anonymity and protection from surveillance. This veil of secrecy makes it an attractive haven for illegal activities. To buy his fentanyl, the man uses “darknet” sites, which are unlisted on search engines, rely on a special private browser for access, and don’t tie his username to his identity.
The Top 6 Deep And Dark Web Credit Card Sites
WeTheNorth is a Canadian market established in 2021 that also serves international users. It offers counterfeit documents, financial fraud tools, hacking and malware services. It has an active forum and community along with an extensive user vetting process. Despite growing crackdowns from law enforcement agencies, the dark web remains a hotbed of criminal activity, offering everything from drugs to stolen data. Remember, engaging in illegal activities on the Dark Web is strictly prohibited. Exercise caution, protect your personal information, and be aware of the risks involved at all times when navigating Dark Web marketplaces.
- Buying illegal substances, stolen merchandise, and counterfeit currency or goods online poses significant risks for both the buyer and the seller.
- Cybersecurity professionals study dark web marketplaces to analyze cyber threats, data breaches, and malware distribution patterns.
- Firstly, using counterfeit money is illegal and can result in criminal charges if caught.
- A lot of vendors from all over the world are registered here, offering an extensive range of products, including digital services, security tools, and other equipment.

Thus, it makes it, even more, comfortable for the terrorists to purchase uranium from the black markets going undetected. There is still a controversy whether it exists in the darknet despite its fame. Some claims to have had experienced the service while the others have flagged it under “scam” or “fake”. Hackers on both excellent purpose and as well as lousy purpose can be hired using the hackers-for-hire service from the dark web. An instance had revealed that people had found a slightly used Gulfstream Jet put up for sale on the most prominent now-defunct deep web market Silk Road.

Criminals use this information for money laundering, opening bank accounts, applying for loans, and draining your finances. Many listings involve stolen personal information, including credit card data, Social Security details, and full identity profiles. As law enforcement agencies’ tactics improve, some markets respond by introducing more security features, like mandatory encryption or invite-only access.
Remember, while evaluating seller feedback and ratings can provide valuable insights, engaging in credit card transactions on the Dark Web is illegal and carries significant risks. It is essential to proceed with caution and prioritize personal security and ethical considerations. It is crucial to approach the Dark Web with caution and fully understand the risks involved. It is illegal and unethical to engage in activities that exploit stolen credit card information. Protecting personal information and ensuring online security should always be a top priority.
Use Cryptocurrency For Transactions
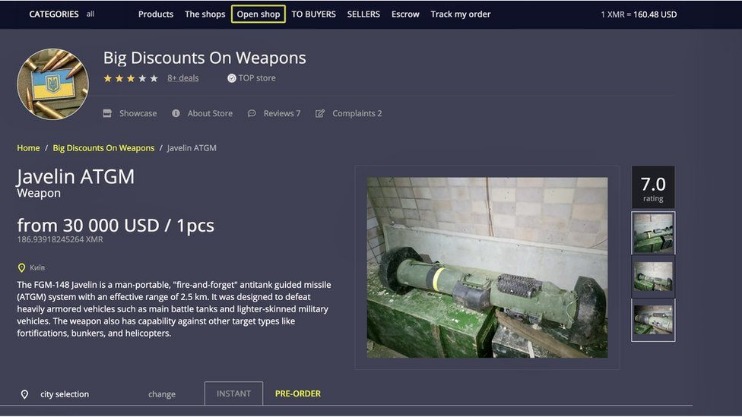
These efforts aim to prevent the illegal trade of weapons and protect public safety. There is a significant danger of purchasing counterfeit or adulterated substances that can have severe health implications. Furthermore, law enforcement agencies monitor dark web activities and have been successful in shutting down various drug marketplaces, leading to arrests and prosecutions. Apart from that, prescription drugs and other supplements are made available on these marketplaces under the drugs segment. We will explain to you using an example for we feel that will be easier for you to understand all the steps.
This includes investigations, arrests, and prosecutions of those involved in these illegal activities. Governments, law enforcement agencies, and international organizations are actively collaborating to combat the trade of fake identities and passports on the Dark Web. This includes efforts to enhance identification systems, improve border control measures, and prosecute those involved in the production and distribution of counterfeit documents. Law enforcement agencies and intellectual property rights holders are actively working to combat the sale of counterfeit goods on the Dark Web.



