
There are a few reasons why the dark web isn’t stopped or shut down. First, it’s difficult to track and monitor activity on the dark web since much of it is encrypted. Journalists and whistleblowers, including Edward Snowden himself, often use the dark web and Tor to exchange sensitive information.
RuTor has extensive threads covering cybersecurity related news, corporate data breaches, and technical tips and techniques for network infiltration and tracking. While people and organizations do host legitimate and useful sites on the dark web, it’s still best to tread cautiously. Despite Tor’s privacy-focused design, malicious entities are more likely to target your data in transit and on .onion sites. Using Tor to access dark web links isn’t illegal, but your ISP will notice, and others may too. It’s, ironically, more conspicuous than using popular browsers and sites.
Choose A Dark Web-compatible Search Engine

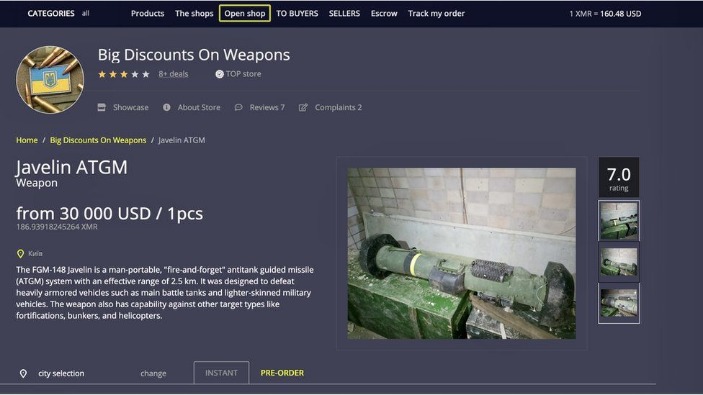
Therefore, we can conclude that OMs are socio-technical structures that facilitate coordination and transactions among buyers and sellers through online media. The dark web, an enigmatic subset of the internet, operates as an encrypted and anonymous network inaccessible through standard web browsers. Unlike the surface web, which is indexed and easily searchable, or the deep web, which houses private databases and unindexed content, the dark web is a haven for covert activities. It facilitates a range of illicit trades, including the sale of stolen data, hacking tools, counterfeit documents, illegal drugs, and firearms.
Despite the security, scams are still a common issue, especially as dark web transactions are final and cannot be reversed. Many users find themselves cheated by false listings or fake vendors, losing their assets without recourse. The Dark Web refers specifically to websites and services hosted inside Darknets. Search engines do not index these sites and use domains like .onion (for Tor) or .i2p (for I2P). Darknet is your best source for the latest hacking tools, hacker news, cyber security best practices, ethical hacking & pen-testing.
The affiliates distribute the ransomware packages through the dark web. These attacks often include stealing victims’ data and threatening to release it on the dark web if the ransom isn’t paid. They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails. Never log in with your real name or reuse passwords from other accounts.

Use Cryptocurrency For Transactions
BreachGuard will guide you through the process of recovering your accounts, helping you lock them down before a hacker can use your leaked credentials. What should you do if your information is found in a data breach or you think it’s been leaked somewhere? Change your passwords and watch out for suspicious activity on your credit reports. The dark web can certainly be dangerous — with no regulation, it’s a riskier place to hang out than the surface web. Malware and scams are scattered like landmines around the dark web.
The 9 Most Private Cryptocurrencies In 2025
The majority of the users on the dark web use the Tor (The Onion Router) browser. A vast number of URLs have domain endings such as “.onion”, which means that the URLs are only accessible by Tor users. We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better. The dark web is a very popular platform for journalists, political bloggers and political news publishers, and in particular, those living in countries where censorship shields most of the internet. But human trafficking, illegal pornography featuring underaged victims, money laundering, and assassinations are also examples of the darkest corners on the dark web. You can also find email messages, online bank statements, and much more information on the deep web – information that is usually private and inaccessible by the public on the surface web.
Is Tor Browser Free?
To safeguard sensitive information, businesses must adopt comprehensive cybersecurity strategies, including regular risk assessments, security gap analyses, and the deployment of tools like dark web monitoring. These measures not only help identify vulnerabilities but also enable swift action to mitigate threats before they escalate. Investing in robust cybersecurity solutions tailored to your organization’s needs is no longer optional; it is essential to ensure operational continuity and maintain stakeholder trust. Law enforcement agencies and international coalitions play a critical role in countering dark web activities. Operations such as the takedown of the Silk Road and AlphaBay marketplaces demonstrate the global effort required to dismantle these illicit networks. However, combating dark web crime demands cooperation between businesses, governments, and technology providers to address emerging threats and protect the integrity of data.

Subscribe To Our Blog For More News And Updates!
You can use dark web monitoring tools, such as NordVPN’s Dark Web Monitor, to check if your data has been leaked. These tools scan dark web forums and marketplaces for any signs of your compromised credentials. There is no need to visit darknet marketplaces yourself to know whether your data was leaked. After that, many other marketplaces kept trying to take its place and become the top dark web market.
- We also conceptualize OBMs as crowd-powered catalyst organizations and recommend LEAs to monitor OBMs dynamics balancing the technological and the social dimensions.
- In fact, a recent judgment by the US Supreme Court denoted that simply using Tor was sufficient probable cause for law enforcement to search and seize any computer around the world.
- Since its inception, the Internet has provided users with an infrastructure enabling different forms of interactions.
- A security gap analysis can help businesses identify vulnerabilities that hackers exploit to compromise their data.
The dark web remains a persistent challenge for law enforcement and cybersecurity professionals. While it offers anonymity and opportunities for illicit activities, it also presents significant risks to individuals and businesses. By understanding the nature of dark web markets and the threats they pose, we can take steps to protect ourselves and mitigate the impact of cybercrime. Dark web marketplaces aren’t just peddling the same old stolen credit card numbers and drugs anymore.
Illegal Pornography
To access the dark web, you’ll need a specific set of tools – more about that later in the step-by-step section. That means that only 0.024% of all the known pages are findable in Google’s search engine. The users only have access to a fraction of the available data and web pages. The content of all these pages is stored on Google’s servers, but it’s mostly outdated, old content; smartphone app content; journals; court records; private social media profiles, and much more. In 2021, a small marketing firm experienced a devastating data breach after employee login credentials were compromised and sold on a dark web marketplace.
The dark web addresses are a randomly-scrambled sequence that generates URLs, mostly hard to remember ones. For example, the URL of Silk Road is rather unintelligible and may look something like “gan4arvj452janndj4a76.onion”. So, that means that the number of pages increased by over 100 trillion in just over three years.
The more informed and vigilant we all are, the better we can tackle the challenges posed by the dark web. A well-informed community is a strong line of defense against these underground markets and their illegal activities. On top of that, undercover operations are a key strategy that’s being used, with agents posing as buyers or sellers to infiltrate these markets. The field of digital forensics also plays an important role since it helps investigations trace digital footprints back to their sources.
To understand how Tor actually works you need to know what happens when you typically search the web. Each time you visit a website, you can be traced back to your exact location thanks to that IP address. However, most are outdated and have not kept up with the changing landscape.
A 2014 study found that the most common type of content found on Tor, the most popular darknet, was child sexual abuse material. Because of its anonymity, the dark web is filled with illegal services and is used by numerous criminal groups, including ransomware gangs. It is also used by whistle-blowers, journalists, and other individuals who are not involved in illegal activity but need to protect their communications and identities. Through the dark web, users in places of high censorship can also access information and news. The dark web contains content that’s only accessible through networks like Tor. Tor browsers create encrypted entry points and pathways for the user, so dark web activity remains anonymous.



