
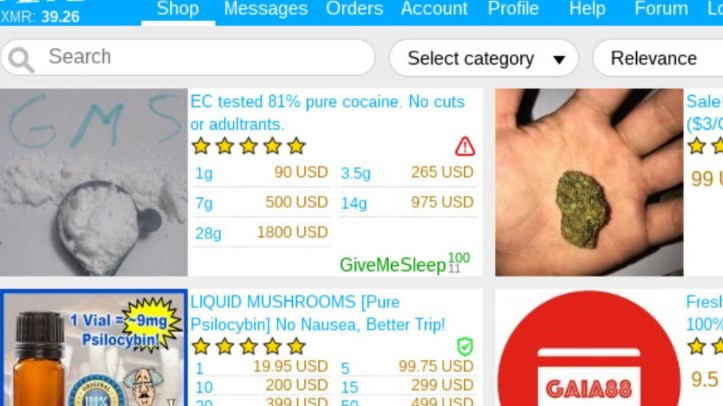
Figure 9 shows some of the listings of compromised accounts being sold at a darknet market. Mixed bitcoins are similar to tumbled bitcoins, but they have been mixed with a larger pool of bitcoins. This process is often referred to as “mixing,” and it can help to further obscure the transaction history of the bitcoins. Some darknet markets may only accept mixed bitcoins, as they provide an even higher level of anonymity and privacy.
Bitcoin: The Dominant Cryptocurrency In The Dark Network
In 2025, alliances between cybercriminal syndicates and state-backed hackers have grown more common. These collaborations increase the scope and impact of attacks, often targeting infrastructure, defense systems, and financial institutions. Rivalries between nation-state actors have also spilled into the dark web, with turf wars emerging between different sponsored groups over control of marketplaces and services. Cybersecurity teams must proactively monitor for leaked data and increase resilience against ransomware and phishing campaigns.

Power Your Insights With Data You Can Trust
The second category consists of data stores, which specialize in stolen information. Today’s cybercriminals spread their activities across multiple platforms, making them harder to track and shut down. In 2023, the dark web attracted an average of 2.7 million daily users, with Germany now leading as the country with the highest number of Tor users, surpassing the United States for the first time in years. Recently, TRM Labs reported that around $2.1 billion in crypto has been stolen in the first half of 2025. According to a July 14 report by TRM Labs, the site, its backup portal, and all related servers have been taken down. Investigators noted that the operators likely shut everything down and left with user funds.
Easy Steps To Access Dark Web On Your Phone Safely In 2024
Decentralized autonomous organizations (DAOs) even govern some of these markets. Such models ensure that the market remains community-controlled and resilient to outside interference. If you believe you have encountered a scam, report it immediately within the marketplace’s community. However, recourse may be limited due to the nature of these transactions. The months and years after Silk Road’s closure were marked by a greatly increased number of shorter-lived markets as well as semi-regular law enforcement takedowns, hacks, scams and voluntary closures. Arguably, the reasons above are why Lightning is not currently integrated into any darknet market.
Top Dark Web Marketplaces Of 2025: A Deeper Dive Into Illicit Trade Markets

Four themes and 14 categories were generated and discussed, including information on accessing the deep web, the Darknet online drug trading sites, search engines, and cryptocurrencies. The paper is a systematic guide for addiction professionals on the deep web and online drug marketplaces. Aside from drugs, illegal wildlife trade also happens on the Darkweb, although the extent of such trade is lower than the open trade on the surface web. Cryptocurrencies have become integral to the dark web economy, enabling illicit transactions and fueling cybercrime activities. Initially, Bitcoin was the primary currency for darknet markets, but its traceability led to the rise of privacy coins like Monero and Zcash, which offer enhanced anonymity.
- While Bitcoin has reclaimed its role as the dominant currency in these markets, its position remains tenuous due to increasing scrutiny from law enforcement and regulatory bodies.
- The global crypto market cap is $3.76T, a 3.66% decrease over the last day.
- However, from June 28 to July 10, 2025, this dropped to USD 13,000 across just 100 deposits.
- Smooth digital asset integration demands a well-considered strategy seasoned with innovation, regulation, and proactive risk management to make a secure financial future a reality.
H Is Available For Trading!

If you ever decide to explore the dark web, protecting your identity is crucial. Most people start by using the Tor Browser, which hides your IP address. Telegram channels supplement traditional onion sites, blurring lines between the dark web sites and more mainstream communication tools. Please note that an investment in crypto assets carries risks in addition to the opportunities described above.
Once Tor sees an address in this format it tries to connect to the specified hidden service. Many darknet market users also use a VPN network to add an additional layer of privacy to hide their source. Additionally, where non-compliant cash out points are facilitating the movement of illicit funds from DNMs, regulators and law enforcement may take action to disrupt activity at the cash out point itself.
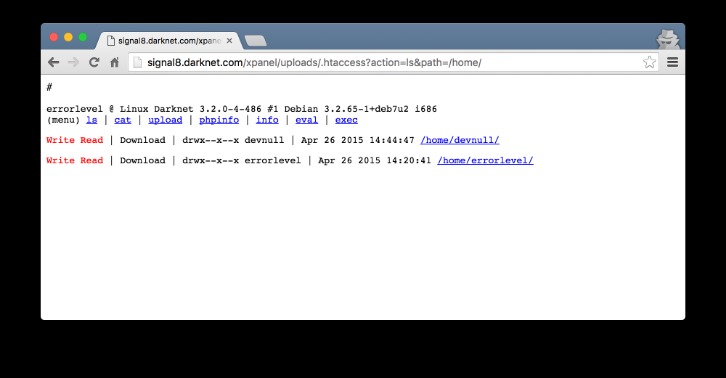
Investigating The Staged Assassinations Of Silk Road
Its interface makes it easy to identify clone websites and ensures that users always use the authentic site. Moreover, the layers of encryption and the bounce of your data from node to node effectively mask your IP address, enabling online anonymity. It allows access to the .onion sites on the dark web that you won’t find using a regular browser. These geopolitical dynamics intensify the complexity of cybercrime, creating multi-layered threats that affect both public and private sectors globally.
Cryptocurrency’s New Frontiers: Dark Web Markets In 2025
The methods take advantage of the pseudonymous nature of cryptocurrencies and evolve constantly to remain one step ahead of regulatory monitoring and blockchain analytics. At KELA, we help you identify and mitigate risks by providing actionable intelligence from the darknet. Our solutions empower you to monitor illicit darknet marketplaces and track emerging threats, ensuring you can take proactive measures to protect your organization and reputation. The darknet is a mysterious and often misunderstood part of the internet, attracting both intrigue and concern. Darknet markets, in particular, have gained attention for their role in facilitating the exchange of illicit goods and services. Despite their controversial nature, these marketplaces continue to evolve, offering a glimpse into the darker side of online commerce.
Since the demise of Silk Road, numerous markets have emerged on the dark web for transactions of hacked passwords, stolen credit cards, compromised accounts, money laundering and fraud-related services. Although the S2S network is composed only of U2U transactions, all categories of sellers (i.e, market-only, U2U-only, and market-U2U) are present in the S2S network. For instance, market-only sellers are entities classified as sellers only in markets, but that may promote U2U transactions with other sellers, hence being part of the S2S network. Therefore, the S2S network can be seen as a proxy for a distribution network of illegal products. Darknet markets, known for illegal activities, are evolving despite regulatory pressures on privacy-focused cryptocurrencies like Monero and ZCash.
The truth is that most people, especially the administrators and merchants of darknet markets, do not care. That’s one of the reasons bitcoin is losing darknet market share to other cryptocurrencies that have figured this out already. Sanctioned nations use cryptocurrencies to evade economic restrictions, conducting cross-border transactions and mining digital assets to generate revenue.
Jardine emphasized that illicit cryptocurrency transactions represent only a minor share of total crypto activity. The largest component of the S2S network of U2U transactions between sellers for each year with the respective number of nodes (N). The nodes are sellers that are active in that year, and an edge is placed between two sellers if at least one transaction occurs between them during that year. The network is mostly populated by U2U-only sellers, followed by market-only sellers. After a major external shock in 2017, the S2S network shrinks but, unlike the multiseller network, recovers, and grows again (though slower than the multibuyer network).
- Eric Jardine, a cybercrime research lead at Chainalysis, noted a substantial increase in Bitcoin inflows into these marketplaces since Monero’s delisting.
- Unchained, your no hype resource for all things crypto by former Forbes senior editor Laura Shin, author of The Cryptopians.
- We highlight that these networks exhibit different resilience regimes in the presence of external shocks, the ecosystem’s resilience being mostly guaranteed by the network of buyers rather than sellers.
- Four themes and 14 categories were generated and discussed, including information on accessing the deep web, the Darknet online drug trading sites, search engines, and cryptocurrencies.
As cryptocurrency evolves, so too does its relevance in various online spaces, including the darknet. By remaining informed and cautious, users can engage with these markets more safely and effectively. Silk Road was utilised by its users as a black market for all types of (in most countries) illegal activities, like buying and selling drugs, credit card data or even guns and other weapons. It was the first Darknet black market of its kind and was the precursor for many similar sites. Conversely, transaction networks obtained from the blockchain contain the entire transaction data of the DWMs and U2U transactions, allowing a thorough investigation of the ecosystem as a whole. In fact, previous studies on DWM transaction networks have revealed crucial aspects of the ecosystem13,14,15.
Purchases in the darknet markets are typically made using virtual currencies like Bitcoin. An individual who wants to buy a product in the darknet market needs to credit his/her darknet market account with Bitcoins to make purchases in the darknet market. The buyer purchases and moves Bitcoins to the darknet user account used by the buyer and makes the desired purchase. Once the buyer has initiated the purchase, the respective cost of the purchase in Bitcoins from the buyer’s account are held in the darknet market’s escrow until the order has been completed. Once the purchase order has been completed, the Bitcoins are released to the Seller (Vendor). The figure below shows a flowchart of the payment model being used in darknet markets.



