The python package “scikit-learn” (Pedregosa et al., 2011) was utilized for training, testing, and evaluating the classifier. Subsequently, we (IV) compare dark web counterfeit prices with prices of the same products on the surface web to understand possible profit margins for the various product types identified. We then (V) compare our results to observations made through border seizures, complaint statistics, and activities from authorities to contribute to the overall understanding of the counterfeit economy. However, as expected, the overall number of offers is much lower, with counterfeits accounting for around 2.69% of all listings across markets.
It assigns a task to the client instead of the server, eliminating server-related vulnerability. It has a feature called CoinJoin that combines multiple coins from different users into a single transaction. This makes it extremely difficult to find out who you are transacting with. Wasabi is one of the most popular cryptocurrency wallets on the dark web.
Government And Institutional Safeguards
Advertised as “the most advanced darknet market ever,” OMG primarily provides illegal drugs, but also offers products like hacking utilities, banking information, and more. It first became active in early July 2020, with deposit volumes so low it appeared to be less of a darknet market and more a personal operation. However, nearly as soon as Hydra shut down, OMG began seeing high inflows for the first time, more than half of which came from Hydra counterparties. The technology and network category includes trust factors regarding the user experience on websites and the smoothness of internet connections. The success of web markets is greatly facilitated by their well-designed and well-structured interface, since the persuasion of customers begins when they first visit the website. The structure and manageability of the website (Al-Dwairi, 2013) and the performance and stability of the market interface (Karimov & Brengman, 2014) both affect the purchasing process on surface web markets.
Use Active Monitoring Of Financial And Identity Theft
Moreover, if you must use public Wi-Fi, ensure that you use a VPN to mask your browsing activity and keep yourself secure. In this era, it takes one wrong click and all your sensitive data ends up in the wrong hands. Therefore, you need to take your privacy seriously and start by using strong and unique passwords for every online account you open. Does allow individual users vending on the platform for USD $60.00 (refundable).
Poker Day Designs Unique Poker Tees, Accessories, And Hoodie Goodies™
It’s important to note that although the dark web has many valuable services, it is also a hangout for cybercriminals. In due course, the framework was remodeled and made public as a secure browser. Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy.
Another website is Dread, which is often called the “Reddit of the Dark Web.” It’s a community platform where users can discuss new markets, share onion links, add reviews, and much more. When the FBI and Europol announced the takedown of Genesis Market in 2023, a site known for selling digital fingerprints, many expected demand to dissipate; instead, buyers and sellers regrouped on Telegram. According to researchers, hundreds of micro-markets sprang up in private channels. Analysts noted that Telegram enabled a shift toward decentralised “broker networks,” where smaller groups coordinated sales of Genesis-style data. This decentralised model makes it far more challenging to target with a single operation. The way darknet actors coordinate has undergone a dramatic shift in the past decade.

Illicit And Risky Use-Cases

The deep web is about 90% of the internet, while the dark web makes up about 5%. A large portion of deepweb links are sites hidden behind security firewalls or authentication forms, such as banking sites or any of the billions of web pages that are password protected. Deep web sites have to be hosted somewhere, and Impreza Hosting is one of the most secure and anonymous dark web hosting services. A host is basically a website’s house, or where it lives and takes up space. Fraud-related products, consumer electronicselectronics, self-defense products, and even hosting.
AzureStrike – Offensive Toolkit For Attacking Azure Active Directory Environments

To reduce scams, many markets also use escrow systems, where the site holds the buyer’s payment until they confirm the item has been delivered. Technological advancements have empowered law enforcement agencies with sophisticated tools to detect fraud effectively, making detection and prosecution increasingly likely. All darknet markets use escrow this basically means the buyer’s payment is held in escrow until the buyer confirms they’ve received the product which gives a piece of mind to the buyer. They also use 2FA, PGP, Private Mirros and Multi Signature to name some of the security features. Kerberos has grown rapidly — some reports note over 1,100 listings within seven months, while others claim 5,000+ listings — showing a strong vendor presence.
- While accessing Darknet Markets themselves is typically not against the law in most places, engaging with illicit goods within them is generally considered a crime.
- Most likely, the native account on your device has full admin permissions by default.
- “This is the single most significant law enforcement disruption of the darknet to date,” U.S.
- Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though).
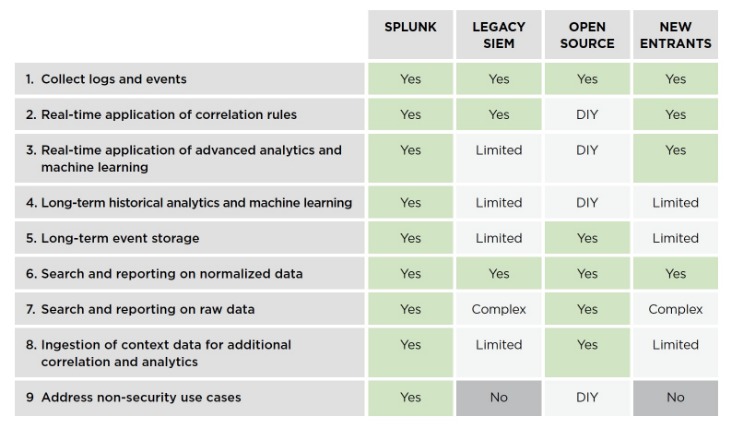
All Markets At A Glance
Law enforcement takedowns, such as Archetyp, demonstrate both impact and adversary adaptation. For cybersecurity professionals, focusing on payment methods, vendor migration, and marketplace specialisation offers the most effective path to actionable intelligence. While darknet markets aren’t entirely risk free they generally offer a much safer alternative than buying drugs or other things in person. For example, AlphaBay Market – once the largest dark web marketplace – was seized by US and international law enforcement in 2017. Hansa Market was covertly run by authorities during the AlphaBay operation.
Thus, estimation of product origins from dark markets and measures of seized goods might also vary because they capture products at different supply chain stages. Cybersecurity companies and researchers monitoring darknet markets face legal and ethical restrictions. Legally, they are limited to observing publicly accessible areas using tools like the Tor browser, without engaging in unauthorized access or illegal transactions. STYX MarketSTYX Market, launched in 2023, is all about financial crime.
Can WiFi Owners See Your Internet History?
Hence, watches might be shipped more diversely, possibly going through different security measures and being more difficult to catch overall. However, single parcel shipments might only be worthwhile for high-value items, such as watches, but less profitable for items that need high-volume sales. Unlike surface web platforms, darknet markets have no reliable way to verify vendors. Many “trusted” sellers use fake reviews or steal reputations from shutdown markets. Of course, not all activity on the dark web is criminal, but such marketplaces are where a lot of illegal trade and money laundering happens. By relying on encryption, pseudo-anonymous currencies, and network-level anonymity, they create a false sense of safety, drawing in both buyers and sellers.
Secure Your Tor Setup
By limiting access to vetted referrals, markets reduce the chances of law enforcement infiltration. In practice, this means potential buyers and sellers may undergo background checks within forum communities before receiving an invite. This layered approach, combining encryption, strict moderation, and personal referrals, aims to preserve the secrecy and continuity of the marketplace. Operational security (OPSEC) extends to how marketplaces and forums vet newcomers and moderate ongoing transactions. Moderators often request proofs of credibility, such as verified PGP signatures, to ensure participants are not infiltrators or scammers. Some platforms employ multi-factor authentication methods, compelling users to provide a secondary passphrase or a one-time code delivered through encrypted channels.
Like ransomware, criminals can buy software and inject your devices with viruses. With it, they can spy on people, steal their sensitive data, or secretly control their devices. These software are also capable of launching DDoS attacks and phishing campaigns. Too-good-to-be-true investment offers are another classic scam on the dark web. Early participants may see some profit, but that money usually comes from new victims, not actual earnings. Eventually, the system collapses, and most people lose their entire investment.
Top Dark Web Marketplaces Of 2025: A Deeper Dive Into Illicit Trade Markets
In tandem with escrow, robust feedback mechanisms allow users to review sellers’ reliability. These rating systems shape market reputations and encourage fair dealing, at least within the confines of illicit trade. Moreover, it aims to examine the goods and services sold on these platforms, shining a light on the evolving tactics vendors use to market stolen data, counterfeit items, and various forms of digital contraband. This information is vital for crafting effective countermeasures, as each new trend or innovation in the Dark Web marketplace raises the stakes for law enforcement and cybersecurity teams. Reddit is a popular platform for discussing a wide range of topics, including darknet markets.



