The .onion domains are the websites that belong to the area of the Internet referred to as the Dark Web. The fact is that, no matter how great the internet is, it is very, very unsafe for regular users. Especially for those who do not have skill in protecting themselves online. Most sites on the Dark Web use the Tor encryption tool to hide their identity.
- The dark web is content that exists on dark nets, which require specialized software (like the Tor Browser), configurations and authorization to access.
- Even though it’s possible to access the dark web using incognito mode, this does not protect your online identity and activities.
- Crawlers can automatically scan websites and their links, then record them.
- According to recent research, Bitcoin tumblers are increasingly used for money laundering.
- Yes, but for .onion sites, you’ll need search engines designed for the dark web like DuckDuckGo’s .onion version.
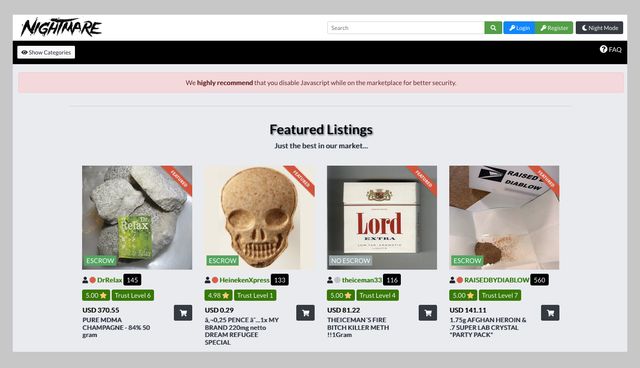
Dangerous And Disturbing Services And Items
It blocks trackers, prevents user fingerprinting, encrypts data, and reroutes your browsing so no one can see where in the world you are. The dark web, for the uninitiated among you, is a virtual neighborhood beyond the borders of the normal, everyday internet (which includes the website you’re looking at right now). It’s somewhere Google and Bing don’t index, and you need special tools to get to it.
How To Access The Dark Web Safely And Anonymously

It is imperative to stay alert and trust your gut when on the web. You should never use your personal information on the dark web anywhere else in your life. In fact, create new throwaway accounts and documents if possible. Ensure you have used prepaid and unidentifiable credit cards when purchasing on the dark web. Avoid using payment methods that can easily expose your identity. Today, many organizations exist that are created only to handle these reports anonymously and effectively.
Safely Browse And Verify Onion Sites

The maximum trouble you can get into on the dark web is visiting political forums or marketplaces. In that case, the government might flag and monitor you even if you’re not a participant or trader. Even if you are not a customer of illegal marketplaces, visiting them can get you on a government watchlist. Although you plan to remain anonymous, slight human errors can crack your anonymity if you are not vigilant enough. Similarly, you can encounter severe issues if you visit a political forum and accidentally leak your identity.
Steps To Install Tor
The company’s website provides detailed instructions on how to use it. Again, we don’t recommend this method, though it might be preferred if the security of Tor exit nodes is of concern. Using a VPN in conjunction with the Tor (The Onion Router) browser is the best way to access the dark web safely. A dark web VPN prevents websites and your ISP from knowing when you’re using the Tor browser.
Legitimate Use Cases For The Average User

This is good practice generally, but particularly important in countries where the Tor browser is blocked, such as China, Russia, Belarus, and Turkmenistan. If your personal information has been leaked on the dark web, your risk of identity theft and financial fraud significantly increases. This is why many people prefer an identity theft protection service and a financial and credit fraud protection solution. By doing so, early signs of fraud can be detected in near-real time, such as new inquiries on your credit file like new credit cards or bank loans. Not all dark web services are genuine, and many scam “.onion” sites offer downloads infected with backdoors and trojan horses.
Dark Web Browsers
- Before engaging in any dark web activities, I recommend researching official dark web sites ahead of time — use your regular browser to look online and see which sites are reputable.
- Unlike the surface web, which can be indexed by standard search engines, the dark web exists on encrypted networks and hosts websites with random, complex URLs.
- It’s not easy to find what you’re looking for on the dark web, especially if you want to do it safely.
- A Tor Browser from the Tor Project is available for Android, and The Onion Browser from developer and journalist Mike Tigas is available for iOS mobile devices, which the Tor Project links to.
- It includes any page that you can find with a simple Google search.
While some reports of dark web murder-to-order are overblown, it is possible to commission acts of cybercrime on the dark web. These range from phishing campaigns to DDoS (distributed denial of service) attacks, which can take down entire servers and websites. You can access the dark web on mobile with a dedicated dark web browser app. Install a mobile dark web browsing app — like Tor browser for Android or the Onion browser for iPhone — and enter an onion URL to start browsing.

Tails never writes anything to the computer’s hard drive, running only from the RAM of the computer, which is wiped clean when the computer is shut down. Users who wish to gain access to such information are protected by the same anonymity the publishers of the content enjoy. Well-known news websites, such as ProPublica, have launched deep websites. Meanwhile, Facebook also offers dark web access to their social network. Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine. To access the dark web, you’ll need a specific set of tools – more about that later in the step-by-step section.
Since their deadline wasn’t met for the closer of the sites a month later, the Impact team ascended to the dark web, where they started to publish the data. The child pornography site Playpen is one of the famous scenarios that resulted from the dark web. The site had only been up and running for about seven months, but surprisingly, it gained over 215,000 users.
The Dark Web is simply a part of the internet that cannot be reached by standard search engines and browsers. To access the dark web safely, it’s necessary to use a dark web browser like Tor in combination with trusted dark web directories and search engines to help you find reliable sites. You should also make sure your device is protected by strong antivirus software, and consider using a VPN to mask your activity on the dark web. That may seem an extreme way to browse the web, but such protections are increasingly worth considering, says Sarah Jamie Lewis, executive director of the Open Privacy Research Society. No, while it hides your IP address and traffic, there are still vulnerabilities.
This creates a privacy risk even if they can’t see what you’re doing on the dark web. Plus, in some regions, accessing the dark web alone may raise suspicion or get you flagged for extra monitoring. The dark web is only accessible through unique dark web browsers like Tor. Tor is a special browser and the most popular choice because of its security features.
One of the best ways for them to protect themselves would include using special, secure, and anonymous networks. Tor network is the perfect example of this, and today, we are going to talk about it, and also about its .onion domains. Law enforcement agencies like the FBI, Europol, and Interpol actively monitor and shut down illegal activities on the dark web. But you can do this through using open-source encryption software such as Veracrypt. Using open-source means there’s far less chance of any security flaws or deliberate backdoors as the code is constantly reviewed by the community.
For instance, there are some organizations who employ the services of white-hat-hackers for a number of reasons. Often, these ethical hackers use their computer savvy to help governments agencies and big corporations hunt down vulnerabilities and in turn, create patches defenses for those system weaknesses. A VPN can help disguise your use of Tor and your visits to dark web resources. If you need to access dark web resources, these are the steps you need to take.
If Tor is not banned in your country, you can directly click the “Connect” button and connect to the Tor network. If it is prohibited, you will need to adjust the connection settings. In the early 2000s, Tor was released to the public and became popular among users who wanted to protect their privacy online.



