
Therefore, you should understand the legal risks of accessing the dark web before you venture into this murky world. On the surface web, you can contact your credit card company or law enforcement for help. But the dark web operates like the Wild West—no rules, no protection. Cybercriminals often disguise malware within legitimate-looking files to trick users into compromising their own security. Once downloaded and opened, these files can install viruses, spyware, ransomware, or other harmful software without your knowledge.
- Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault.
- If you’re just browsing the dark web out of curiosity, Tor, or a Tor and VPN configuration is safe enough.
- This button will reload the site with a new circuit, which may solve the connection issue.
- Within the dark web, there are various hidden websites, known as darknet markets, where illicit goods and services are bought and sold.
- Just like Google, the dark web has some search engines present on it.
Unraveling The Truth About The NIST’s New Password Guidelines
These features are accessible from the Freenet interface under the “Community” and “Tools” sections. Designed to be hidden from conventional search engines like Google or Bing, the dark web is a portion of the internet. Access to “.onion” domains and anonymous surfing made possible by specialised software like the Tor Browser allows entry only.
How To Access The Dark Web Safely: A 2025 Beginner’s Guide
These tools remove reliance on central registrars and servers, allowing dark web sites to persist across mirror nodes even after a seizure. While adoption is early, the shift signals a long‑term move toward censorship‑resistant infrastructure. Operational security, or OPSEC, is the discipline that turns technical anonymity into real‑world protection. Tor and VPNs mask your network path, but a single careless click can still expose your identity.
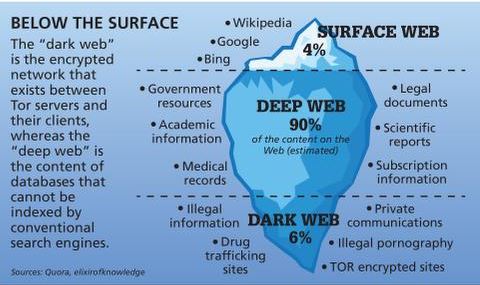
- The dark web is a subset of the deep web that is intentionally hidden, requiring a specific browser—Tor—to access, as explained below.
- A VPN will give you an extra layer of protection and anonymity, making it much safer to explore the dark web.
- The Darknet offers a place of free expression where not even a chunk of these limitations exists.
- The dark web is part of the internet that is not indexed by standard search engines like Google, Yahoo, and Bing.
- This means you have to know someone who is already using the platform.
Marketplaces For Everything Illegal
“Bitcoin has been a major factor in the growth of the dark web, and the dark web has been a big factor in the growth of bitcoin,” says Tiquet. The affiliates distribute the ransomware packages through the dark web. These attacks often include stealing victims’ data and threatening to release it on the dark web if the ransom isn’t paid. Upgrade your lifestyleDigital Trends helps readers keep tabs on the fast-paced world of tech with all the latest news, fun product reviews, insightful editorials, and one-of-a-kind sneak peeks. Pushing your hardware to its full potential — such as by enabling XMP — ensures that you get the best performance which is crucial for all sorts of heavy tasks including gaming. Memory is one of the key components that can bring a noticeable improvement in video quality and speed.
Is It Illegal To Enter The Dark Web?

It will normally take a while to connect because Tor — unlike other browsers — will route your traffic through different nodes. You should also keep in mind that overall speeds will likely be impacted; for example, a page might take a few seconds longer to load than what you are used to. The Tor network is operated by thousands of volunteers worldwide who maintain the proxy servers that protect your identity.
Experian is a globally recognized financial leader, committed to being a Big Financial Friend—empowering millions to take control of their finances through expert guidance and innovative tools. As a trusted platform for money management, credit education, and identity protection, our mission is to bring Financial Power to All™. Louis DeNicola is freelance personal finance and credit writer who works with Fortune 500 financial services firms, FinTech startups, and non-profits to teach people about money and credit.
While no method guarantees complete anonymity, you can minimize the chances of being tracked with the right precautions. As a general rule, it’s best to use the default settings in Tor or the Onion Browser. Changing any of the default settings can make websites misbehave or not load correctly. The Dark Web and Darknets offer valuable spaces if you value privacy, freedom of speech, or research security technologies.If you misuse them, the consequences can be severe.
Is Using The Tor Network Illegal?
For deeper access or full Tor anonymity, you can also stack NordVPN with the Tor browser for double encryption, and during testing, everything stayed stable. These are the final stops in the Tor relay chain before your traffic hits the open web. Anyone running a malicious exit node could potentially monitor, manipulate, or inject content into your session, especially if you’re visiting non-HTTPS sites. The browser routes your traffic through a global network of volunteer-run servers (sometimes called nodes), encrypting your data and masking your IP address multiple times. Unlike Tor, however, it cannot be used to access the public internet. It can only be used to access hidden services specific to the I2P network.
FAQs About Accessing The Dark Web Safely On Your Phone
As digital ecosystems morph, staying informed and agile will help you make the most of evolving privacy tools—or avoid stepping into ever-more complex traps. Open up Tor, and you won’t suddenly see the dark web staring back at you. Not only do you need a dark web browser, you need a dark web search engine too. This search engine will get you to the sites you need, though you can also go directly to dark web addresses if you know what they are, as with standard URLs. Tor is like the public-facing door to the dark web, and there are even mobile apps for Android and iOS.
The threat can extend to your entire network of devices connected to the internet. Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people. Moreover, malicious actors can attempt phishing scams to steal your data and identity for extortion. Simply put, accessing and browsing the dark web is perfectly legal.
Law enforcement, meanwhile, leverages blockchain tracing, undercover buys and server misconfigurations to stage high‑impact busts that temporarily inflate prices and spur copycat platforms. Such spaces let researchers and activists trade defensive know‑how without exposing their real‑world identities. Inside Tor, every hop is encrypted, but if you visit a non‑HTTPS surface‑web page, the segment from the exit relay to that site travels in clear text. Think of it as the courier handing your unsealed letter to the recipient’s mailbox.
Fraud and scams run rampant on the dark web, including offers too good to be true and fake services requiring upfront payment. Hackers sell access to email accounts, social media profiles, or other information that can be used for identity theft. It’s possible to buy and sell illegal drugs, malware, and prohibited content in darknet marketplaces. Some dark web commerce sites have dangerous chemicals and weapons for sale. The websites you visit every day aren’t all there is to see on the internet — not even close.
What Can I Do If My Personal Information Is On The Dark Web?
Buy login credentials to a $50,000 Bank of America account, counterfeit $20 bills, prepaid debit cards, or a “lifetime” Netflix premium account. It’s not easy to find what you’re looking for on the dark web, especially if you want to do it safely. You should only ever access websites you know are safe because they’re vetted by websites or other sources that you already know are safe. Good starting points are the Onion Directory and the Hidden Wiki.
If you want to access the dark web, your first step toward a more private experience should be to secure your internet connection and data with a reliable VPN. Lokinet is easier to set up than I2P, and it may run faster than Tor in some cases, especially when visiting regular websites through its secure network. However, its network is still small, and there aren’t many hidden services available yet. Don’t log into any real accounts, reuse usernames, or enter any personal details. Treat every site as untrusted unless you’ve verified it from multiple sources. The Dark Web remains a shrouded corner of the internet—an enigmatic space where privacy, free speech, criminality, and censorship resistance intersect.



