After all, it’s much less popular, can’t be used to access normal websites, and isn’t as easy to use, among other disadvantages. Both rely on a peer-to-peer routing structure and layered encryption to make browsing private and anonymous. Unlike Tor, however, it cannot be used to access the public internet. It can only be used to access hidden services specific to the I2P network.
Best Dark Web Search Engines For Android & IOS
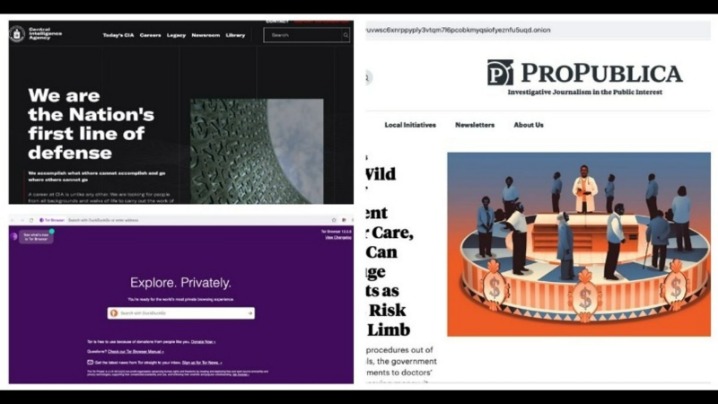
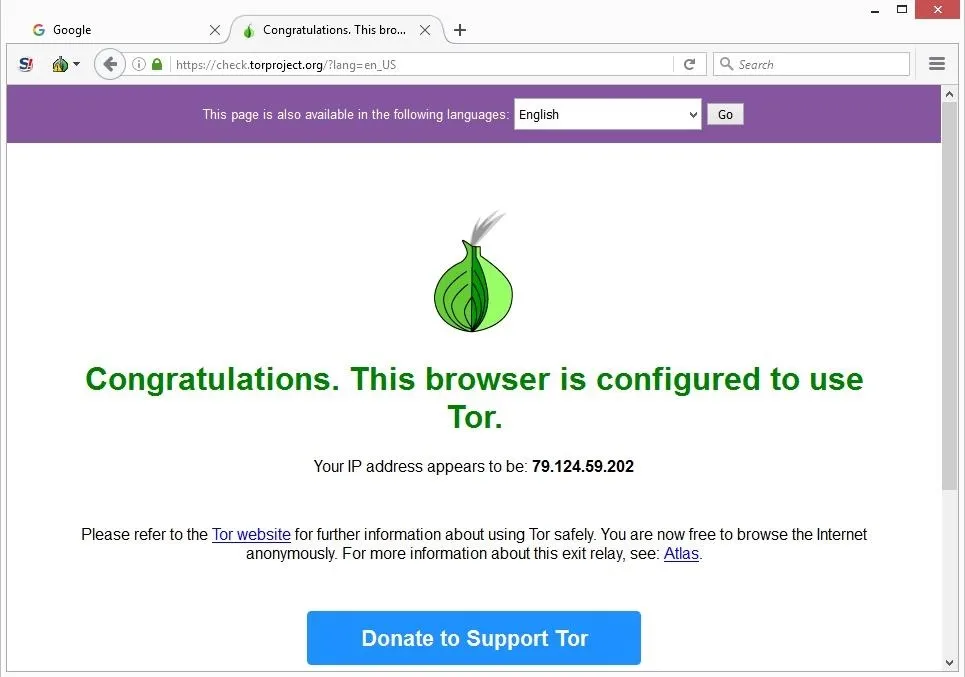
The dark web is home to the internet’s hidden sites, services, and products — some innocent, others downright dangerous. Read on to learn the pros and cons of the dark web, how to access it, and get tips for staying safe. Then, install Norton 360 Deluxe to get AI-powered scam detection to help secure your browsing against online threats. This will help you to remain anonymous and secure at all Tor entry and exit nodes. It uses TrustedServer technology on the entire server network to wipe out your data after every session.
Myth 1: The Dark Web Is Only Used For Illegal Activities
Bad actors can compromise nodes, with exit nodes being of particular concern. On its own, Tor obscures your IP address by bouncing online requests through multiple servers, similar to how a VPN routes your traffic through an external server. Websites you visit via Tor will see the IP address of the exit node, not your actual IP, just like websites see the IP address of your remote server when using a VPN.
How Does Personal Info End Up On The Dark Web?
These secure communication platforms improve your security when using Tor. A traffic correlation attack takes serious resources, but it’s doable for advanced actors with sufficient motivation. A common inquiry from Tor users is if they should use a VPN to add an extra layer of protection.
Step 4: Access I2P Sites (Eepsites)
There are a number of services and tools available on the dark web, many of which can be used for nefarious purposes. The release of Freenet in 2000 is considered by many as the start or founding of the dark web. University of Edinburgh student Ian Clarke created Freenet as a thesis project. Freenet was originally intended to provide a way to anonymously interact online, providing ways to communicate, exchange information and files, and to otherwise communicate incognito. But human trafficking, illegal pornography featuring underaged victims, money laundering, and assassinations are also examples of the darkest corners on the dark web.
Download Tor Browser
Your decisions, responsible conduct, and awareness of potential risks will determine your experience in this hidden realm. Accessing the Dark Web can expose you to a range of risks that might not be immediately apparent. While many visitors manage to browse hidden services without incident, staying safe requires constant vigilance.
Best WiFi Security Protocols: Which One Should You
While Tor is the most common method for accessing the dark web, I2P and Hyphanet offer alternative options for secure and private browsing. Let’s go through the setup process for each, as well as how to use them effectively. In this setup, the VPN connection acts as a middle layer between your device and Tor, routing your internet traffic through the VPN before it reaches the Tor network. If you want to improve your security further, you could also use a VPN at the same time as Tor.
A good antivirus software can detect, quarantine, and remove threats before they can damage your device or acquire any sensitive information. My favorite antivirus in 2025 is Norton, which scored a 100% protection rating during my tests (handily beating the built-in protections on my devices). It also adds an extra layer of anonymity, which is particularly important when browsing the dark web.
Doing so can tie your activity back to you, destroying your anonymity. If you need to create accounts on dark web services, use a burner email and never reuse usernames or passwords from your real life. If you must purchase anything on the dark web — which I don’t recommend — you should always pay in cryptocurrencies.
Especially for those who do not have skill in protecting themselves online. But with the NSA setting up fake exit nodes, and growing concerns about the overall security of the network, you may need a VPN as well, if you want to ensure your privacy. If you’ve already done that, or even something similar, that’s good news – you’re already a deep web user accessing information not available through common search engines. Everything from social media data to medical records are held on the deep web, as is all your email information. Subgraph OS is a Linux-based operating system designed for security, privacy, and dark web access. Built with multiple layers of security and Tor integration, it provides a robust environment to prevent malware attacks and safeguard user data.
- The advantages of I2P are based on a much faster and more reliable network.
- The “VPN-over-Tor” approach offers added protection, even if Tor is compromised.
- The dark web presents various threats, including malicious software and computer viruses, posing risks to users’ systems and data security.
- It assigns a task to the client instead of the server, eliminating server-related vulnerability.
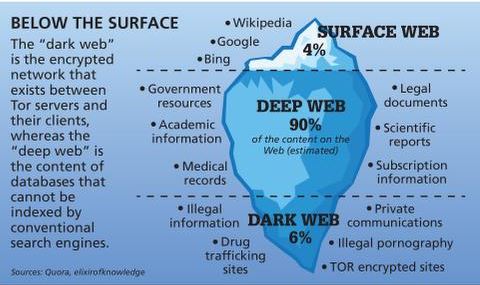
- The deep web includes non-indexed databases and private portals, while the dark web specifically requires Tor and includes .onion sites.
How It Works: Tor Over VPN
Are Wi-Fi hosts and owners able to see what you’re doing online? Most likely, the native account on your device has full admin permissions by default. Many malware take advantage of this vulnerability to launch an attack. Therefore, you can prevent this exploitation by setting up a non-admin account. If you are in a position to report the incident safely, you should report it to the authorities immediately.
How Do I Recognize Phishing Sites On The Dark Web?
With HTTPS, only you and the website you’ve requested can see the information being exchanged on your browser. This setting forces all website connections to use the secure HTTPS protocol rather than HTTP, an insecure version that leaves you vulnerable to eavesdropping. DuckDuckGo uses its web crawler and also curates data from over 400+ sources, including Google and Bing. Hence, you’ll see accurate search results similar to searching on Google. You can download the Tor browser from the official website, Torproject.org.
Drugs, weapons, and stolen IP and data are all hot businesses on the dark web, with terabytes of information on offer. Traders cash in on stolen credit card data dumps, initial access points to vulnerable systems, credentials, and intellectual property belonging to companies compromised during cyberattacks. Our editors thoroughly review and fact-check every article to ensure that our content meets the highest standards. If we have made an error or published misleading information, we will correct or clarify the article. If you see inaccuracies in our content, please report the mistake via this form.
These are platforms where leaked or stolen data, including personal information, passwords, and credit card details, are bought and sold. They often provide access to vast amounts of compromised data from previous hacks or breaches. Data breaches happen all the time, and your login credentials and other data might be on the dark web already. Avast BreachGuard scans the dark web and will alert you immediately if and when it detects your personal data. BreachGuard will guide you through the process of recovering your accounts, helping you lock them down before a hacker can use your leaked credentials. Later, Tor’s underlying code was released under a free license, and a nonprofit called the Tor Project was formed.



