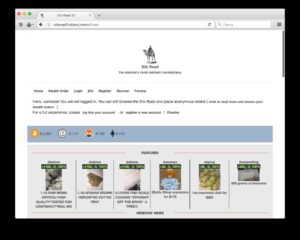
Search engines do not index these sites and use domains like .onion (for Tor) or .i2p (for I2P). If you’ve heard of the dark web and the deep web, it’s important to know these aren’t exactly the same thing. The deep web is made up of sites that won’t show up on internet searches. The dark web adds another layer of secrecy to this, in that you need a special browser to access sites there. The Dark Web has long been shrouded in mystery and intrigue, often portrayed in popular media as a haven for illicit activities and shadowy dealings. As we move into 2024, it’s crucial to separate fact from fiction and understand the realities of the Dark Web, especially in the context of the United Kingdom.
Spotify Introduces Groundbreaking New Feature That’s Dividing Users
Moreover, the dark web is a small portion of the deep web that is unavailable on search engines, making it difficult to monitor. Even though the dark web is famous for its illegal use, it is not controlled by a single person or organization. But your ISP will only know you are using Tor and cannot see what website you are visiting with it. It is crucial to remember that using Tor is not illegal, but engaging in cyber-terrorism or other unlawful activities through it is.

Criminal Who Laundered Money For Romance Scammers Jailed

Note that Tails’ installation package is the .img format, which means that you’ll need software capable of burning images on your thumb drive. Tor relays are servers run by volunteers, designed to keep your activities private and untraceable. Unlike regular browsers that directly connect to websites via your ISP’s DNS, Tor anonymizes your journey by routing your request through several relays before reaching its destination. Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny.
Protect Your Devices With Strong Security Software And Practices
There’s legitimate activity on the dark web too, as activists, journalists, and whistleblowers use dark web forums for anonymous communication. These forums look similar to those found on the clear web, but the content discussed and shared by the anonymous chatters can evade censorship on public sites and surveillance. The problem is that getting to those forums may require opening yourself up to safety concerns like the ones listed above. Even in an era of increased online surveillance, the average person on the internet likely has too much to lose to bet on their safety for curiosity’s sake. Heck, I’m one of PCMag’s resident security experts, and I’m not playing around on the dark web just because I know how to. That’s why I’m not going to provide links or detailed instructions for accessing the internet’s shadier side.
The Role Of Cybersecurity On The Dark Net

Of course, it’s a completely legitimate app offering end-to-end encrypted messages and calls so that ISPs and other third parties cannot access the users’ data. There are many other reasons, apart from buying drugs, why people would want to remain anonymous or set up sites that can’t be traced back to a physical location or entity. People who want to shield their communications from government surveillance may require the cover of darknets. Whistleblowers may want to share vast amounts of insider information to journalists without leaving a paper trail.
Why Security Leaders Prefer To Buy CTI Solution For SaaS Platforms In 2025
Action Fraud is the UK’s national reporting centre for fraud and cybercrime and more details about specific types of cyber fraud is available from Action Fraud. Computer Misuse Act 1990 (‘CMA1990’) is the main UK legislation relating to offences or attacks against computer systems such as hacking or denial of service. A DoS attack is an attempt to make a machine or network resource unavailable to its intended users, to temporarily or indefinitely interrupt or suspend services of a host connected to the Internet. In January, state police in Latvia set up a separate unit, external specialising in monitoring chat apps for drug trafficking and communication, and officials have named Telegram as a particular concern. Criminals like the dark web because of the anonymity it provides – internet traffic is bounced around the world, obscuring people’s locations.
As a rule, a package sent from Eastern Europe arrives in Saint Petersburg in 14 days, from Central Europe – in 18 days, from Western Europe – in 21 days, from North America – in 30 days. I suspect the same extension of delivery time is valid for other countries. Darren Guccione is the CEO and co-founder of Keeper Security, the world’s most popular password manager and secure digital vault. Keeper is the first and only password management application to be preloaded with mobile operators and device manufacturers including, AT&T, Orange, America Movil and HTC. Keeper has millions of consumer customers and the business solution protects thousands of organizations worldwide.
- I review privacy tools like hardware security keys, password managers, private messaging apps and ad-blocking software.
- On the other side, the software used to access it, Tor, is not an illegal browser.
- Immediately close your entire Tor Browser window (not just that active tab).
- In this blog, we’ll navigate the dark web verse and how you can protect your digital assets while surfing in it.
- MLA is generally used for obtaining material that cannot be obtained on a police cooperation basis, particularly enquiries that require coercive means.
- Educate employees about cybersecurity best practices; including recognising phishing attempts and following secure data handling procedures.
Salesforce Data Missing? It Might Be Due To Salesloft Breach, Google Says
In addition, the content on the pages don’t need any special or custom configuration to access. Typically, any reference to the visible web will be to common websites with a familiar internet domain extension. Google considers the majority of the content on the entire web highly irrelevant and useless to its users. That’s why such a large percentage (as much as 94%) of the entire web is not returned in Google Search. Customers frequently think about how they want their orders delivered before making a purchase. Some people will rent a mailbox to receive the shipment if they are worried that the authorities will seize it on the way to their home address.
- Check your online accounts’ privacy settings to ensure you’re sharing only necessary information.
- Even if you’re using a private, anonymized crypto wallet, there are other ways your identity can be revealed—even if it’s something as simple as letting a personal detail slip in an instant message.
- For safer browsing, it is highly recommended to also use a VPN and antivirus software.
- In the evolving landscape of digital technology, the “Dark Web” is a term that has managed to pique the interest of many, sometimes with shrouded layers of mystery.
Man Who Created Computer-generated Child Sex Abuse Images Convicted
Some of these sites are very helpful (but unseen as Google doesn’t show them), while others are just for fun. And personal cybersecurity also needs to be something which staff at all levels are taught about – from new joiners, to board members. But as business owners, cybersecurity experts and individuals, you can do a lot to help too.

The UK Cyber Security Group is committed to keeping digital spaces safe for businesses and individuals alike. We believe that awareness and education are the first steps to prevention. Cybersecurity professionals play a crucial role in monitoring and mitigating the threats that originate from the dark net. While the overall volume of dark web transactions remains relatively small compared to global illicit commerce, the rapid growth and severity of these crimes have become a major concern for authorities. The Dark Web and Darknets offer valuable spaces if you value privacy, freedom of speech, or research security technologies.If you misuse them, the consequences can be severe. Unlike the Deep Web, Darknets are intentionally hidden and designed to preserve privacy and anonymity.
Buy login credentials to a $50,000 Bank of America account, counterfeit $20 bills, prepaid debit cards, or a “lifetime” Netflix premium account. Research revealed that a piece of stolen personal data costs an average of £289 on the dark web. This price varied depending on the type of data and whether it was physical (e.g. a forged document) or digital (e.g. credit card information).
As part of our ongoing efforts, we promote “Cyber Essentials” – a government-backed scheme that provides a foundational set of guidelines and practices for organisations to bolster their cyber defences. Engaging with the Cyber Essentials program ensures that even if your data is compromised and finds its way into the dark corners of the internet, the potential harm can be mitigated. The very nature that allows for protection of privacy and free speech also provides a haven for criminal activities. Their efforts help to identify, mitigate, and prevent a wide range of cyber-attacks, ultimately enhancing the overall cybersecurity posture of the organisations they serve. Finally, you need to enter website addresses to access content on the dark web since you can’t browse by entering a search query as you can on the clear web.

Cryptocurrencies such as Bitcoin have been the dark web currency even before they became available to the general public. Right now, you can use many cryptocurrency .onion sites to buy or sell all types of cryptocurrencies. This is the best place to get short and reliable links to an unalterable record of any webpage across government and corporate websites. Formerly known as Archive.is, it is one of the best onion sites on the dark web. It aims to preserve the internet’s scientific and cultural heritage.
Immediately close your entire Tor Browser window (not just that active tab). Note that engaging with the content in any way is not only distressing but could also put you at legal risk. This is because law enforcement often actively monitors these sites. These sites are a hybrid tutorial-underground where wannabe hackers ask questions and professionals sell their services or stolen data. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship. The anonymity provided by onion routing comes at the cost of slowing your internet considerably.