
A VPN provides strong security for everyday browsing without the extra delays, middle checkpoint, and then finally the exit gate. The extra connection layers can act as a significant burden to your browsing experience if you’re doing something that is bandwidth intensive. This sequence offers less anonymity because your real IP address is still partially exposed along the Tor path.
- The Escrow’s .onion link provides a platform for conducting anonymous transactions on the Dark Web by holding funds securely until agreements are fulfilled.
- The “surface web,” on the other hand, is the publicly available part of the internet that search engines index.
- Wasabi Wallet allows you to manage Bitcoin transactions anonymously using the Tor network.
- Its affordability and reliability have earned it a loyal customer base.
- Husain Parvez is a Cybersecurity Researcher and News Writer at vpnMentor, focusing on VPN reviews, detailed how-to guides, and hands-on tutorials.
- The dark web is not easily accessible, especially with browsers like Chrome or Safari, as it requires specialized protocols like Tor’s onion routing.
What Is The Safest Dark Web Search Engine?
To access the dark web, you will need the Tor browser, which provides the necessary anonymity and security. Activists, whistle blowers, and journalists also use the dark web to communicate securely with sources and news organizations. Impreza Hosting is a service that helps you host a site on the Tor network. It provides an .onion URL and an interface for you to manage your Tor site easily. It also boasts that no personal information is required to use the service, and payment can be made with cryptocurrency. Keybase also offers extremely user-friendly secure chat and file-sharing services through its app.
Dark Web Monitoring And Identity Theft Protection At Your Fingertips
But if you use antivirus software, avoid clicking shady links, and stick to known sites you should be okay. It’s also a good idea to set up a VPN for an extra layer of protection. Most dark web links are hosted on “.onion” domains due to the sensitive nature of the businesses or services they host. Tor websites may provide secure access to cryptocurrency wallets and anonymous email clients, and they’re also used to access black market sites. Dark web websites are not indexed by standard search engines and can only be accessed using specialized tools, such as the Tor web browser. These sites provide a level of privacy and anonymity unavailable on the surface web, offering content and goods that cannot be easily found through traditional online platforms.
Use Active Monitoring Of Financial And Identity Theft
For all these reasons, at PrivacyRadar, we strongly discourage using Awazon or any other dark web marketplaces. It’s for the good that these sites are not available for the general internet user. The marketplace has an intuitive interface and offers powerful search tools that make it easy for you to find products from both local and international sellers. All vendors are vetted before they are allowed to sell, so it makes sure of trust and quality. Because it’s a members-only platform, you’ll need to register first.
What Are The Best Onion Sites?
It is a good way to prevent third parties from tracking online activities. People in countries with heavy internet censorship must get a VPN or Tor browser to access the surface web. For instance, services like ProtonMail and SecureDrop (mentioned above already) have hidden sites for their users who live in countries with high levels of censorship. It will offer you an additional layer of encryption to access the deep parts of the internet. Check out these best onion sites to access the dark web securely and anonymously. Since you cannot access a library of dark web links using the regular Internet, you can check out platforms dedicated to indexing these sites, like The Hidden Wiki.
Please note that all material provided here is aimed at promoting awareness, responsible research, and ethical use of information. A curated collection of darknet resources for educational purposes, offering insights into darknet frameworks, tools, and security practices. As part of the raid, the website was identified as being hosted on a private server located inside Son’s bedroom in South Korea. Further inspection revealed logs containing over one million Bitcoin addresses. Even referring new users allowed “privileged” access to the content. The website, which has now been taken down, has led to agencies seizing nearly 8TB of unique and gravely disturbing data.

Unlike other websites hosting images of child sex abuse, ‘Kidflix’ allowed users to stream videos as well as download files. Once you have the Tor Browser installed, launch it and click “Connect.” That’s it! Keep in mind that because Tor encrypts your traffic, your internet speeds may be slower than usual.
DuckDuckGo Onion Search
Plus, it’s slower since your data travels through the same four steps – entry node, relay node, exit node, and then the VPN server. As we mentioned above, when you connect to Tor your data first goes through an entry node, which can see your IP address. By connecting to a VPN before using Tor, you mask your real IP address before it reaches this entry node, adding an extra layer of security and anonymity. All you need to do is click connect and you are officially connected to the Tor network and can now access dark web websites. Feather is a free and open source Monero wallet available on most major computer platforms.
Ahmia — Tor Search Engine With Robust Abuse Protection
While some .onion sites provide essential services like secure communication and censorship-free journalism, others spread malware or run scams. With this in mind, finding verified links is crucial for avoiding threats on the dark web. If you get a reliable vendor, you should procure the services to stay safe when accessing the dark web.
The New York Times
The deep web is made up of email platforms, workplace portals, subscription services, and banking websites — basically anything that requires a login. The “surface web,” on the other hand, is the publicly available part of the internet that search engines index. However, there are many websites engaged in highly illegal or harmful activity. To protect your data from the websites you visit, one of the most effective steps is to hide your IP address, which can reveal your location, identity, and browsing habits. Using a virtual private network (VPN) masks your real IP by routing your internet traffic through a secure server, making it appear as though you’re browsing from a different location. A VPN also encrypts your connection, keeping your data safe from surveillance and unauthorized access.
How To Access The Dark Web
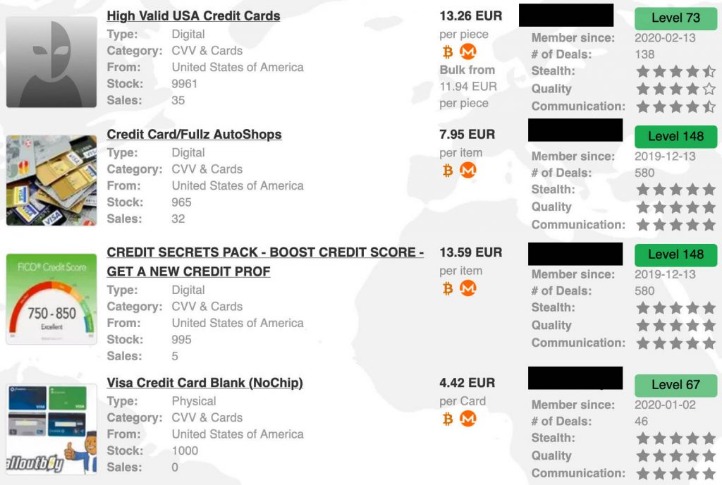
mark it means it has been verified as a scam service and it should be avoided. Fortunately, you can’t just stumble onto dark web websites by accident. No, it isn’t illegal to browse the dark web, and there’s nothing inherently wrong with visiting a Tor website. Stay private with a tool like Surfshark’s Alternative ID to mask your contact details and use generated data on sites you don’t trust. Given the above threats, it’s a good idea to use Tor over a VPN to access the dark web.|It also offers works of art, course material, and audiobooks for download. The process costs a fee, but unlike other “tumbler” or “mixing” services, there is no risk that Wasabi or any of its users could scam you out of your coins. Following the NYT, the BBC launched a dark web “mirror” of their international edition in 2019. Note that some features of the normal website are not available on the .onion version, including BBC iPlayer. It will route your traffic through multiple servers instead of one, making tracking your data and activities even harder.}
Facebook’s dark web version allows users to access the site where it is banned or restricted. Although the social application is known for collecting data on its platform, it does not like sharing the information with others. Dark web browsers and search engines do a lot of work to mask user identities, but you’re never completely untraceable. Not to mention that anonymity safeguards won’t protect you from other threats like hacking and malware. The Dark Web is a dangerous place – You should exercise extra caution when exploring. Our search engine at GOTDW is here to help you explore more safely, but we still urge extra caution as you dive in.

The site, described by officials as being “among the first of its kind to monetize” child porn using Bitcoin, was driven — and funded — by cryptocurrency. Son was arrested by Korean, American, and British authorities in South Korea on March 5, 2018. The 23-year-old had previously been identified after law enforcement discovered Welcome to Video hadn’t concealed its server’s IP address, which they later learned was registered in his name. Authorities seized Son’s server, which contained hundreds of thousands of child porn videos. The National Center for Missing and Exploited Children is now combing through the mountain of content.



