Also, you should ensure that the HTTPs-Only Mode in all Windows options is selected in the security settings to ensure a secure and encrypted connection between the Tor browser and the websites you visit. Though there are other ways to access onion websites, it is recommended that you always use Tor to access dark web websites. It offers better speed and security than other alternative methods. Many people use it for privacy-focused communication, whistleblowing, or accessing restricted information in censorship-heavy regions. Platforms like SecureDrop even allow journalists to receive tips anonymously.
Facebook’s onion mirror allows people to access it in countries that block the platform, allowing people to connect across digital borders. That said, the social network’s data collection and tracking practices may seem at odds with many of the principles motivating dark web users. Concerns about how Meta treats user data have led many people to delete their Facebook profiles or at least limit their social media presence. No, as the Tor network is not good for torrenting — some Tor browsers block P2P traffic, and even Tor’s developers ask users not to use the network for P2P downloads.
Use Active Monitoring Of Financial And Identity Theft
However, it’s much harder to get at the people who are doing the uploading and downloading. Even if you’re using a private, anonymized crypto wallet, there are other ways your identity can be revealed—even if it’s something as simple as letting a personal detail slip in an instant message. Your traffic is relayed and encrypted three times as it passes over the Tor network. The network is comprised of thousands of volunteer-run servers known as Tor relays.
Use Encrypted Communication Apps
- Additionally, check the Block pop-up windows and Warn when websites try to install add-ons settings.
- Tor is one of the easiest and safest ways to access the dark web, which is unavailable to normal “surface web” browsers.
- All Tor Browser data is encrypted and relayed three times over the Onion Router network, which is composed of thousands of volunteer-run servers, which are known as Tor relays.
- The Tor browser is able to access the special domain names, with the suffix .onion, used in the dark web.
- Connecting to the Tor network might raise eyebrows depending on who and where you are.
This information can be used to target ads and monitor your internet usage. Also, there’s a vast amount of unsavory content on the dark web, as well as a significantly high number of hackers and scammers looming on the platform. This type of government surveillance applies mostly to countries with environments that are hostile to free speech. You can either sell or buy goods on the dark web, but both present difficulties.

Installation
Always conduct your own research or check with certified experts before investing, and be prepared for potential losses. Opinions expressed herein are those of the authors and not necessarily those of Analytics Insight, or any of its affiliates, officers or directors. The dark web is just misinterpreted; it is not intrinsically dangerous. Used ethically, such as for privacy or study, one can search this area lawfully and safely. Combined with smart surfing behaviour and technologies like Tor and a VPN, even the darkest reaches of the internet may be securely traversed. Routing your VPN traffic through a Tor connection is referred to as VPN over Tor.
Top 13 Dark Web And Deep Web Forums – Quick List
During my tests, ExpressVPN’s military-grade encryption and verified no-logs policy provided consistent protection against tracking and monitoring. The kill switch feature also ensures your real IP stays hidden if your connection drops. While it doesn’t index dark web content, it’s the default search engine on the Tor Browser because of its strong privacy features and lack of tracking. For searching within the dark web, specialized tools like Torch are better, as they specifically index .onion sites and hidden content. Venus crawls and gathers a wide array of onion sites, ensuring you have access to the latest information available on the dark web.
Step-by-Step Guide: How To Access The Dark Web Using Tor Browser
- This can make it difficult to view certain kinds of content, particularly streaming audio and video.
- Clicking on this prompt will automatically reload the website and redirect the user to its onion counterpart, providing a more secure and private connection through the Tor network.
- The .onion site has thousands of downloadable comic books ranging from niche to mainstream.
- TorBook aims to be a privacy-focused alternative to mainstream social networks.
- The fact that it discusses vulnerabilities, legal tools, data leaks, and malware attracts prominent threat actors constantly.
Onion URLs generally contain a string of seemingly random letters and numbers. Once you are certain that you have the correct URL, save it in an encrypted note—the Tor browser will not cache it for later. Otherwise, there’s a good chance of falling victim to a phishing scam like this fake Bitcoin mixer. Keeping your VPN and Tor Browser updated ensures you benefit from the latest security patches. Outdated software can have vulnerabilities that may put you at risk.
Don’t Provide Personal Information
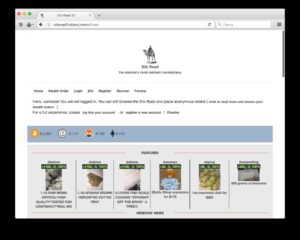
It’s a place where you’ll find data leaks and illegal trades, but also legitimate, legal online activities users want to carry out without attracting the attention of law enforcement agencies or governments. It’s a part of the internet that’s less regulated and more shadowy, for better and for worse. However, while visiting the dark web itself isn’t against the law, engaging in illegal activities there is. The dark web contains a range of content, some of which is illegal, including marketplaces for drugs, weapons, stolen data, and other illicit services. The dark web is home to the internet’s hidden sites, services, and products — some innocent, others downright dangerous.

The Tor Browser works by routing internet traffic through a global network of server nodes to mask your IP address and activity. It encrypts data multiple times, each layer peeled off by a different node, helping to enhance user privacy and making tracking or surveillance extremely difficult. The dark web is also rife with scams, phishing attempts, and fraudulent services.
Stay Anonymous While You Browse

ProPublica is one of the safer Tor sites to visit, because it doesn’t link to illegal content or activities. Instead, it focuses on publishing stories and holding powerful institutions accountable. Other major news sources blocked in some countries, like the BBC, also have dark web versions. And anyone (including your ISP) can see that you’re connected to Tor.

It is a relatively new provider but offers better features than most established VPNs. The provider also offers a dedicated CyberSec suite that prevents annoying ads and blocks malware and trackers. Also, use an effective antivirus program to check threats if you decide to download files. You can check out this guide on the best antivirus software applications today. You should never use your personal information on the dark web anywhere else in your life.

Be cautious of downloading it from unofficial sources, as they may provide modified versions that could compromise your security. After completing these steps, Tor Browser will open, and you will be ready to start browsing the internet anonymously. Tor Browser is pre-configured with privacy settings optimized for secure browsing, so you can enjoy a higher level of anonymity right from the start.