This step-by-step guide is designed to help beginners navigate this hidden part of the internet safely and securely. The most common of these browsers is Tor, which launched in 2002 and serves millions of users. Another is the Invisible Internet Project (I2P), which specializes in the anonymous hosting of websites on the dark web.
Step 2: Download And Install Tor Browser
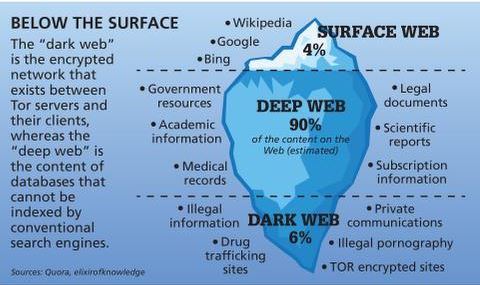
The deep web is in between the surface web and the dark web, and it constitutes the large majority of the actual internet. Similar to the surface web, users don’t need any special software to access the deep web, and it’s a relatively quiet landscape in terms of cyberthreats. A step-by-step guide to safely accessing the dark web while maintaining your anonymity and security. Though not entirely shoddy, the dark web has a reputation for hosting illegal activities. It does support whistleblowers by offering them anonymity and secure communication in an oppressive regime. But navigating the dark web is full of cybersecurity and legal challenges.
Tor’s anonymity function is used by everyone from human rights workers and journalists through to drug and arms dealers. Whether your search engine of choice is Google, Bing, Baidu, Yahoo! The true internet – that which includes content not indexed by these search engines – is hundreds of times bigger.
How Do I Access Tor?
You must use a secure web browser that prioritizes privacy and security and can access onion sites. Even though it’s possible to access the dark web using incognito mode, this does not protect your online identity and activities. While the surface and deep web can be accessed this way, the dark web requires special software.

Security And Practical Recommendations
Lastly, The Hidden Wiki is a collection of dark web links — but the links may not work and can lead to dangerous websites. Surface web search engines can’t access the darknet, but specialized dark web search engines can help you find what you’re looking for. DuckDuckGo is a popular privacy-focused search engine that doesn’t track you across the web. DuckDuckGo’s dark web search engine may index pages on the dark web, but you’ll need to open it with Tor Browser.
How To Remove Duckduckgo From Google Chrome
- PCMag is obsessed with culture and tech, offering smart, spirited coverage of the products and innovations that shape our connected lives and the digital trends that keep us talking.
- In short, the deep web is about restricted access, whereas the dark web is about engineered anonymity.
- IOS is the only exception, leaving iPhone and iPad users without the option to go to this part of the internet.
- Finally, it lets you appear as if you’re browsing from a specific country (the country the VPN server you’re connected to is in).
- After all, it’s much less popular, can’t be used to access normal websites, and isn’t as easy to use, among other disadvantages.
Despite its legitimate uses, cryptocurrency’s untraceable payment nature has raised concerns around money laundering and illicit trade, driving regulatory scrutiny. Bitcoin is the most widely recognized and utilized cryptocurrency on the dark web. Think of the internet as an iceberg, with the visible portion representing the surface web, and the massive, unseen sections representing the deep web and dark web.
Components Of DOT Security’s Services

At a minimum, users should ensure that their cybersecurity defenses are activated and up to date. The deep web is significantly larger than the surface web and includes all the content that isn’t indexed by traditional search engines. This isn’t as mysterious as it sounds; the deep web encompasses everything from your private email accounts and online banking information to subscription-only websites and academic databases. The surface web is the part of the internet most of us interact with daily.
What Percentage Of The Internet Is Dark Web?
Accessing the dark web requires more than just a standard web browser. Before downloading your dark web browser, though, there are a series of safety precautions you’re going to want to take first. This process, though, can often involve accessing the dark web for research into the most current malware on the market.
The Future Of Anonymity And Privacy Tools
This is an extra precaution that can protect your device from savvy hackers looking for any opening that presents itself. Once you’ve chosen a VPN provider and have successfully set up your account, you’re ready to start looking at overlay networks. Malware, ransomware, and hacking tools are widely sold in underground forums. Additionally, check the Block pop-up windows and Warn when websites try to install add-ons settings. Additionally, many Internet Service Providers (ISPs) flag Tor usage as suspicious and may block access to the network altogether.
What Is Tor?
Understanding the Dark Web and its access tools, such as Tor, is crucial for anyone considering exploring these hidden parts of the internet safely and responsibly. This essentially just makes certain that your VPN is working and that your personal IP address isn’t exposed for malicious actors prowling the dark web. To conduct this check, just turn on your VPN and head over to ipleak.net and dnsleaktest.com to see if the IP address displayed is the one from your VPN. The dark web is full of malicious actors, cybercriminals, and other people who are looking to prey on curious but unprepared dark web browsers. By defining your goal and purpose, you won’t find yourself wandering down the dimly lit corners of the dark web, and you can stay on the path you set out for yourself.
- The history of the Dark Web is intricately tied to the development of internet technology and the ongoing pursuit of online anonymity.
- It tends to conjure vague notions of bad people secretly doing bad things.
- But, like I2P, Freenet won’t give you access to .onion links — only content uploaded to Freenet.
- We also recommend using a virtual private network (VPN) such as NordVPN — the best dark web VPN — to add an extra layer of protection.
- If your device is unprotected, you could be a victim of malware or a hacking attack.
Silk Road was one of the first dark web marketplaces and it allowed users to trade multiple types of nefarious goods and services, including weapons and identity fraud resources. While many dark marketplaces have been shut down by authorities, new ones soon appear in their place. The deep web is made up of content that search engines such as Google do not index.
I’ve put together detailed guides on how to access the dark web safely on both Android and iOS. I also share essential tips for staying secure there — personally, I always use a VPN for added privacy since Tor isn’t completely secure on its own. The victim types in their information, thinking they’re accessing a site that they know and trust, but they’re actually giving away their data. There are a lot of these sites across the dark web, which is why you have to be extra careful. The easiest way to avoid falling victim to them is to simply not provide any personal data when browsing the dark web. It’s legal to access the dark web in the U.S. and most other countries.



