
Over the course of crawling and exploring fraud on the darknet and deep web, DarkOwl discovered a unique language across vendors and key fraud cybercriminals operating in this sphere. Darknet marketplace advertisements of counterfeit and digital goods include numerous types of data for sale. Darknet forums and marketplaces are replete with how-to guides, mentors, bank drops, and sensitive PII and credit card databases for sale. Straightforward as it may seem to understand the current fraud landscape – especially with these listings and discussions being so common – the reality is not so simple.
While SSN, name, and DOB are all fairly standard in fullz, other information can be included or excluded and thereby change the price. Fullz that come with a driver’s license number, bank account statement, or utility bill will be worth more than those without, for example. Infosec Insider content is written by a trusted community of Threatpost cybersecurity subject matter experts. Each contribution has a goal of bringing a unique voice to important cybersecurity topics. Unless you live the rest of your life only paying with cash, you’ll never be totally impervious to payment fraud. You may have never been to the dark web — but there’s a chance your credit card information has.
How The Hidden Wiki Works
When engaging in any transaction, it is essential to take protective measures and precautions to safeguard personal information and privacy. This includes using a secure and anonymous internet connection, using a reputable VPN (Virtual Private Network), utilizing trusted marketplaces and vendors, and practicing good online security hygiene. Now that we understand why individuals are enticed to buy credit cards on the Dark Web, let us explore the risks and challenges involved in these transactions and how to navigate this treacherous landscape. There are several darknet hidden services and deep web domains that specialize in trading “fullz”.
What Are Deep And Dark Web Credit Card Sites?

Monitoring the deep and dark web becomes imperative for proactive defense against such threats. Lunar, our dark web monitoring tool is designed to empower individuals and businesses in this battle against cybercrime. With features like real-time alerts, data breach monitoring, and comprehensive dark web post monitoring, Lunar helps organizations stay ahead of deep and dark web threats in an increasingly hostile digital environment. The BidenCash stolen credit card marketplace is giving away 1.9 million credit cards for free via its store to promote itself among cybercriminals.
DarkOwl has observed this with young scam-rappers such as Teejayx6, as shown in the video below. BleepingComputer has discussed the authenticity with analysts at D3Lab, who confirmed that the data is real with several Italian banks, so the leaked entries correspond to real cards and cardholders. The analysts claim these cards mainly come from web skimmers, which are malicious scripts injected into checkout pages of hacked e-commerce sites that steal submitted credit card and customer information.
Why Do Cybercriminals Hack PayPal Accounts?
- This is why regular monitoring of one’s credit score, particularly to watch for any “known addresses” listed in the report that do not belong to the credit holder, is a strategic action to take in detecting identity fraud.
- Due to its extensive inventory and reputation for reliability, Brian’s Club has maintained a significant presence on the dark web.
- DarkOwl assesses fraud against government docs, benefits, and employment will increase since the pandemic.
- Still, they should combine it with other resources to cover a broader range of sites.
- There’s also a privacy angle—some users live in countries with censorship or surveillance, and the dark web gives them a space to communicate or access information more freely.
OnionShare is a popular open-source tool that allows users to share files securely and anonymously via Tor, widely used by activists and journalists for confidential document distribution. The Tor Project’s official onion site offers secure downloads of the Tor Browser and developer resources, helping users access and contribute safely to the Tor ecosystem. These platforms underpin the technical infrastructure necessary for dark web functionality. Beginning in September 2021, Abacus Market has established itself as one of the leading dark web marketplaces. After AlphaBay closed, Abacus Market took its place as the world’s largest underground darknet marketplaces.
Why Our Site Is Better: Up-to-Date, Secure, And No Tracking
Over the past decade, Joker’s Stash emerged as one of the most infamous dark web marketplaces, gaining notoriety for illicit transactions and offering a plethora of stolen financial data. The platform, distinguished by the sophistication of its administrators, left an indelible mark on the cybercrime landscape, and became the central marketplace for stolen card data, outclassing all competitors. Digital banking has transformed both consumer banking and the threats posed to banks and their customers.
Shuttered Dark Web Marketplaces
Meanwhile, the operators behind UniCC will be seeking to cash out their formidable profits. Established in 2022, WizardShop is one of the biggest data stores on the dark web, focusing mainly on carding and financial data. Established in 2022, Torzon market is one of the biggest and most diverse marketplaces on the dark web.
Privacy Advantages Of The Hidden Wiki
Hidden Wiki was originally the name of a .onion hidden service on the Tor network, hosting a directory for links to websites on the Tor dark web. Torzon Market has established itself as a significant player in the darknet ecosystem, offering a secure, user-centric platform for anonymous trading. Its commitment to privacy, diverse product offerings, and robust security measures make it a preferred choice for users seeking discreet transactions within the darknet. Russian Market has consistently remained one of the most popular and valuable data stores on the dark web. The platform’s activity has increased significantly over the past year, indicating its growing influence and market share in the underground economy. Due to its extensive inventory and reputation for reliability, Brian’s Club has maintained a significant presence on the dark web.

Physical cards are usually cloned from details stolen online, but can be used to withdraw from ATMs. Because the merchant requires equipment to clone the card and must send the buyer a physical product complete with PIN number, the price for cloned cards is much higher. AllWorld.Cards appears to be a relatively new player to the market for selling stolen credit-card data on the Dark Web, according to Cyble.

“The most important thing is for people to keep an eye on their transactions and report any fraud immediately,” Krebs says. One of the largest known underground shops, Joker’s Stash, generated more than $1 billion before getting shut down in February, according to Gemini Advisory. A 2019 data leak of another shop, BriansClub — which appears to have been by a competitor, according to Threatpost —shows how pervasive this trend has become.
Freshtools was established in 2019 and offers various stolen credentials, accounts, and host protocols like RDP. It is considered a go-to site for malware purchasing, providing keyloggers, trojans, and other Malware as a Service products. STYX Market focuses specifically on financial fraud, making it a go-to destination for cybercriminals engaged in this activity. Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem. Thank you for joining us on this exploration of credit card transactions on the Dark Web.
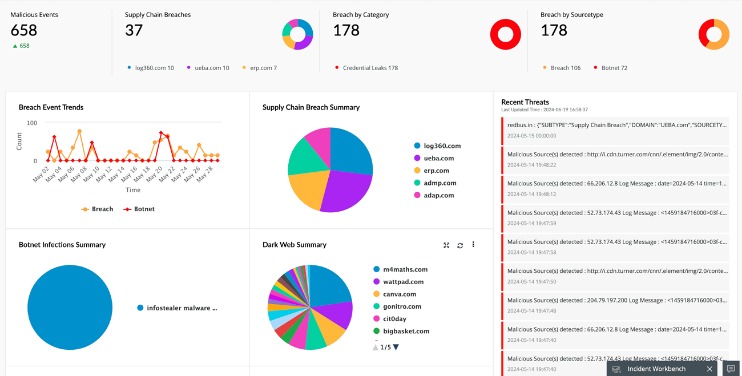
How To Build And Run A Security Operations Center (SOC Guide) – 2023
The Dark Web provides a platform where fraudsters can monetize stolen credit card information, posing a significant threat to individuals and financial institutions alike. Skimming is a type of credit card information theft that involves installation of a small device attached to a legitimate credit card transaction device, such as a credit card machine at a merchant, gasoline pump, or ATM. When the card is inserted or swiped for the legitimate transaction, the card data including the full number, expiration, and card holder’s name is harvested and rerouted to the malicious cybercriminal’s computer or networked server.
These cards can be used to make purchases online or in-store, and can even be used to withdraw cash from ATMs. Although it monitors hacker forums, its coverage remains limited, as it does not track some of the key platforms listed in our Top 10 Dark Web Hacker Forums. The channel states that all shared content is sourced from open internet platforms and intended for educational purposes, disclaiming responsibility for any misuse of the published information. The Tor Browser looks and feels similar to a regular web browser but is configured to prioritize privacy and security by default. It blocks browser trackers and resists fingerprinting, which helps maintain your anonymity while browsing.



