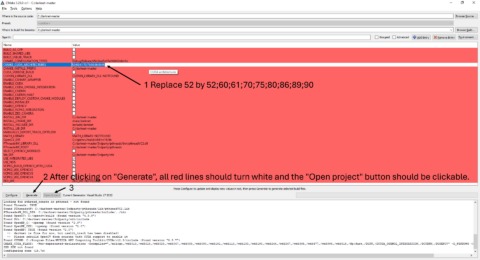
While a threat actor doesn’t generally care about the type or size of the organization they target, their motivation generally, although not always, points to the victim. Understanding these motivations helps to plan effective cybersecurity strategies. Distributed Denial of Service (DDoS) attacks overwhelm a target’s network or system with vast amounts of traffic, which makes them inaccessible to users. Dark web hackers often use botnets to carry out DDoS attacks, causing disruption and financial loss for their targets.
Why Addressing Legacy IT Is An Urgent Strategic Priority For CISOs

It has been in operation for more than a decade since its debut in 2014. Brian’s Club is one of the best place to buy stolen credit card info, including CVVs, dumps, and even full account packages without revealing your identity. You can even find things such as BIN checkers and PayPal cookie converters. Another reason the Russian Market is so popular is that it’s pretty inexpensive compared to other dark web marketplaces. Now, that is not to say illegal behavior is completely beyond detection. The dark web combines encryption, anonymity, and hidden doorways to provide the perfect sanctuary for such illicit activity compared to the usual internet, which is more vulnerable and trackable.
For instance, we see single vendor shop revenue spike beginning around March, around the same time traditional darknet market revenue began to fall. Similarly, single vendor shop revenue fell concurrently with the recovery of traditional darknet markets from around June through end of year. Sanctioning the various actors in the global cryptocurrency laundering and cashout ecosystem has caused disruptions for these services. Monero and Bitcoin are two of the most commonly used digital currencies on the dark web markets. Due to being the most popular and the oldest coin, Bitcoin is traceable. However, Monero, on the other hand, is untraceable and the most trusted payment method on these markets.
Email Services
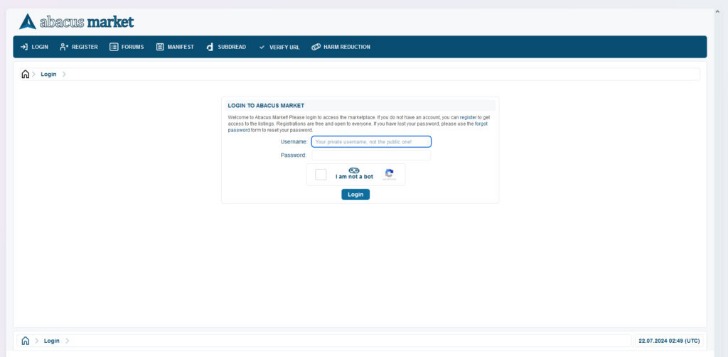
This marketplace accepts payments via Monero but also supports the Escrow system. Using a reliable VPN provider helps keep you safe when you access marketplaces on the dark web. A VPN encrypts the data traffic and keeps your activities private on the dark web. It also masks your IP address, making it difficult for government agencies to monitor or track your activities. We recommend using NordVPN as it offers top-notch security features, including dark web threat protection. The bold mass extortion attempt comes just days after Incognito Market administrators reportedly pulled an “exit scam” that left users unable to withdraw millions of dollars worth of funds from the platform.
Estimates Of Illicit Transaction Activity DO NOT Include:
Additionally, credentials are not required to view content on this site, which is uncommon on most DNMs. Therefore, it is a good site to explore if you do not want to create credentials and/or are new to the darknet. It is usually uncommon for darknet sites to allow you to view products on their sites without eventually facing a paywall.
- One of the most popular uses of the darknet is for online marketplaces, also known as darknet markets or DNMs.
- Reach out to members of the darknet community and improve your research thru these forums.
- Meanwhile, retail vendors, who operate on a smaller scale, are holding more of their illicit earnings in personal wallets, delaying conversion to fiat to avoid detection.
- While hard statistics are scarce, darknet markets have continued gradual growth for years.
- It’s an ever-evolving ecosystem—constantly shifting, reinventing itself, and adapting.
Darkweb Markets 2025: Actual Information And Statistics
Its emphasis on user anonymity and document forgery makes it a core tool for identity fraud. Founded in 2014, BriansClub remains one of the oldest and most infamous dark web markets for stolen credit cards, fullz (complete identity kits), and dumps. The Dark Web is a part of the internet that remains hidden from traditional search engines like Google or Bing. Unlike the surface web, which is easily accessible through standard web browsers, the dark web requires specialized software, such as the Tor browser, to access. It is a hub for financial cybercrime and offers a wide range of illicit services and stolen data that cater to sophisticated cybercriminals. This can include taking down websites and servers used to host these markets, as well as seizing cryptocurrency wallets used to conduct transactions.
Darknet Markets Darknet List 2025 Darknet Market Links Darknet Market Links In 2025
While regulations and law enforcement efforts are increasing, the decentralized nature of the dark web makes it difficult for authorities to completely shut down these illegal marketplaces. As a result, it is important for buyers and sellers to stay informed and take precautions to protect themselves and their information. These subreddits are a valuable resource for anyone interested in darknet markets.
Darknet markets are online platforms that operate on the darker corners of the internet, often facilitating the trade of illegal goods and services. These markets use specific software, such as Tor or I2P, to ensure user anonymity and secure transactions. Cybercrime enablement represents flows from ransomware, stolen funds, malware, or fraud shops to darknet markets.
- KEY TAKEAWAYS Whether you are using Android or iPhone, you can easily access the dark web on your ph…
- We hypothesize that the true damage of scamming is greater than what reporting to the FBI and our on-chain metrics show, but overall, scamming is down, given broader market dynamics.
- The move sparked a boycott among thousands of Reddit communities angered that the change would kill off third-party apps many use to read and post on the site.
- Privacy-focused operators are shifting to Monero due to its default anonymity, compared to Bitcoin’s transparent ledger Darknet markets see BTC inflow drop to $2B.
- Torzon Market has established itself as a significant player in the darknet ecosystem, offering a secure, user-centric platform for anonymous trading.
Why Are All The Darknet Markets Down
While they offer a convenient way for criminals to buy and sell illegal goods and services, they also pose significant risks for users. As we approach 2024, it’s important to stay informed about the current state of darknet markets and the efforts being made to shut them down. By exercising caution and doing your own research, you can help protect yourself and stay safe online. Despite these efforts, it’s unlikely that darknet markets will disappear anytime soon.
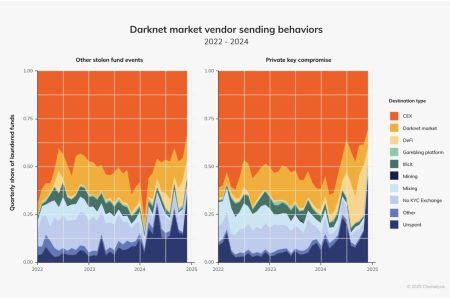
These dealers are likely to step up sales activities on the underground market. As a result, we can expect a continued rise in these deceptive practices, posing a persistent threat to online users. The landscape of “loader” malware services is anticipated to continue its evolution, offering increasingly stealthy loaders to cybercriminals. These loaders, which act as an initial vector for malware infections, pave the way for deployment of stealers, various remote access Trojans (RATs), and other malicious tools. The key capabilities of these loaders are expected to include robust persistence mechanisms, fileless memory execution, and enhanced resistance to security products.

Use Cryptocurrency For Transactions
However, this can be challenging due to the decentralized nature of the darknet market and the use of anonymizing technologies. One approach that has shown promise is the use of undercover operations and sting operations. By infiltrating darknet markets and posing as buyers or sellers, law enforcement agencies can gather intelligence and make arrests. However, these operations are resource-intensive and can be difficult to execute. The anonymity and lack of rules that define darknet marketplaces are exactly what make them breeding grounds for fraudulent activities.
Mercedes-Benz Head Unit Security Research Report
We developed Lunar to monitor the deep and dark web, including dark web marketplace sites. However, you can trace its roots to the development of technologies like the Tor network or Freenet. In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet. This was the initial framework for anonymous communication and file sharing. Later in 2022, the US Naval Research Laboratory built on Freenet’s idea to create a secure and encrypted network for sensitive communications, which was later released to the public as open-source software.
Why Brand Monitoring And Threat Intelligence Are Stronger Together: 15 Key Benefits
FreshTools, founded in 2019, specializes in selling stolen account credentials and data, particularly webmail, RDPs (Remote Desktop Protocols), and cPanels. The platform is favored by cybercriminals seeking access to accounts that can be exploited for fraud or sold to others. Founded in 2020, Cypher Market has carved out a niche on the dark web by focusing on cybercrime products.
The authors and the website are not liable for any financial losses or legal issues resulting from the misuse of this information. We analysed a novel dataset of Bitcoin transactions on 31 major dark marketplaces and investigated how the dark marketplace ecosystem was affected by unexpected marketplace closures between 2013 and 2019. The dark marketplaces we considered were heterogeneous in many ways and 24 of them were closed abruptly due to police raids and scams. We found that the total volume traded on these dark marketplaces dropped only temporarily following closures, revealing a remarkable resilience of the marketplace ecosystem. Archetyp Market was dismantled in June 2025 during Operation Deep Sentinel in a coordinated raid across six countries.
Typically, we only include measurable on-chain activity in our estimates for illicit activity. In the case of FTX, it is impossible to use on-chain data alone to measure the scope of the fraudulent activity, as there’s no way to isolate illegitimate movements of user funds. As such, we believe the $8.7 billion in creditor claims against FTX is the best estimate to include. Given the size and impact of the FTX situation, we are treating it as an exception to our usual on-chain methodology. If courts convict in similar, ongoing cases, we plan to include their activity in our illicit transaction data as well in the future. In addition to counterfeit merchandise, MGM Grand Market offers access to stolen credit card information, compromised bank accounts, and other financial fraud-related services.



